
The Challenges
I’ve always been a huge fan of forensics related challenges, particularly those that are memory dumps where I get to use volatility. It’s not too common and I’ve only come across a few that present a great deal of challenge. The team over at HackerOne did a fun one with the Veteran’s CTF but the challenges from HeroCTF had at last weekend were awesome and some real mind benders. Below are the prompts and their solutions.
We need you 1/5
There were a couple ways to solve this one.
You could run the strings command and grep for “COMPUTERNAME” or use Volatility
String is the quickest and arguably least painful method if I’m being honest.
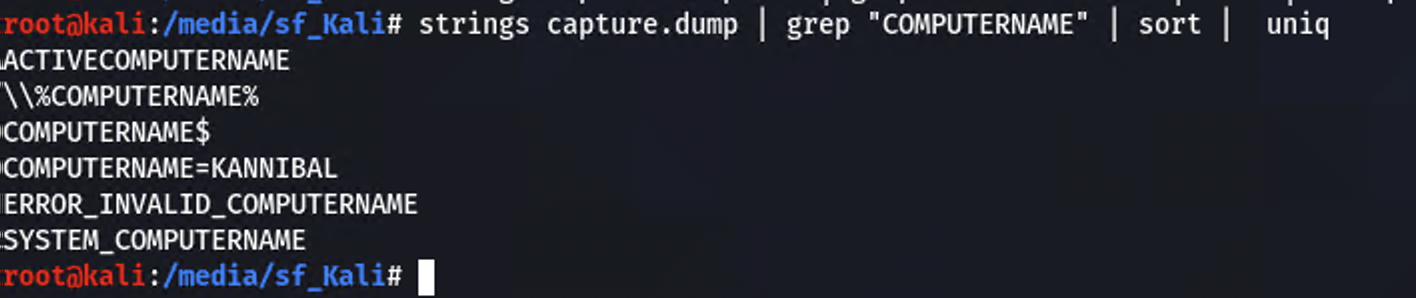
strings capture.dump | grep “COMPUTERNAME” | sort | uniq
The remaining challenges require volaitlity so might as well identify the flag with volatility as well.
The memory dump file will include a dump of all registry hives loaded into memory. By locating the SYSTEM hive it’s possible to pull the hostname from the “ComputerName” registry key.
volatility –profile=Win7SP1x86 -f capture.dump hivelist

With the virtual address identified, query the specific registry entry to extract the hostname.
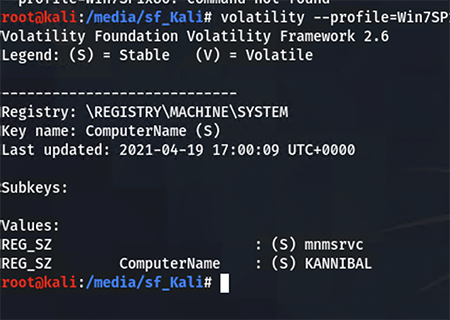
volatility –profile=Win7SP1x86 -f capture.dump printkey -o 0x8941a2c0 -K “ControlSet001\Control\ComputerName\ComputerName”
Flag:
Hero{KANNIBAL}
We need you 2/5
This challenge is relatively straightforward if you utilize the “hashdump” module from volatility. There are 3 users and the prompt does ask for the “user’s” password but you’ll notice only Razex has a password entry as the other two have an empty password.

volatility –profile=Win7SP1x86 -f capture.dump hashdump
Cracking the NTLM hashes (notice the empty password):
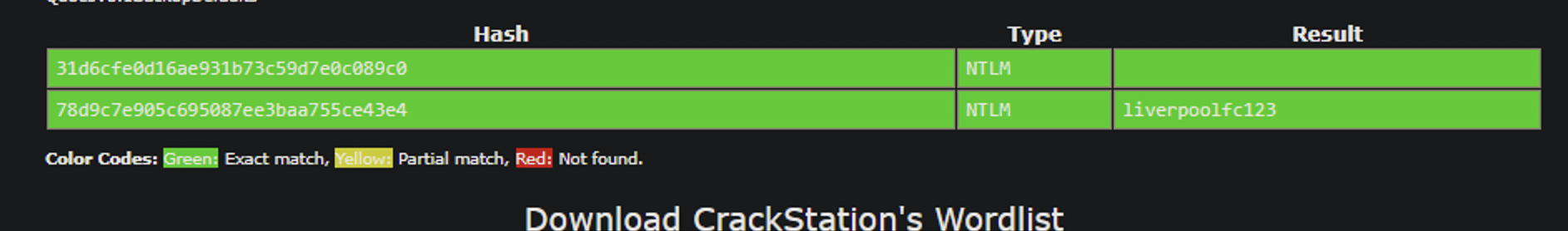
Flag: Hero{liverpoolfc123}
We need you 3/5
I found the answer to this one by mistake while just enumerating the image file. The “cmdscan” module can extract the command history from the memory dump. In the command history is a netcat executable lisetening for an incoming connection and also making an outbond to “146.59.156.82”.
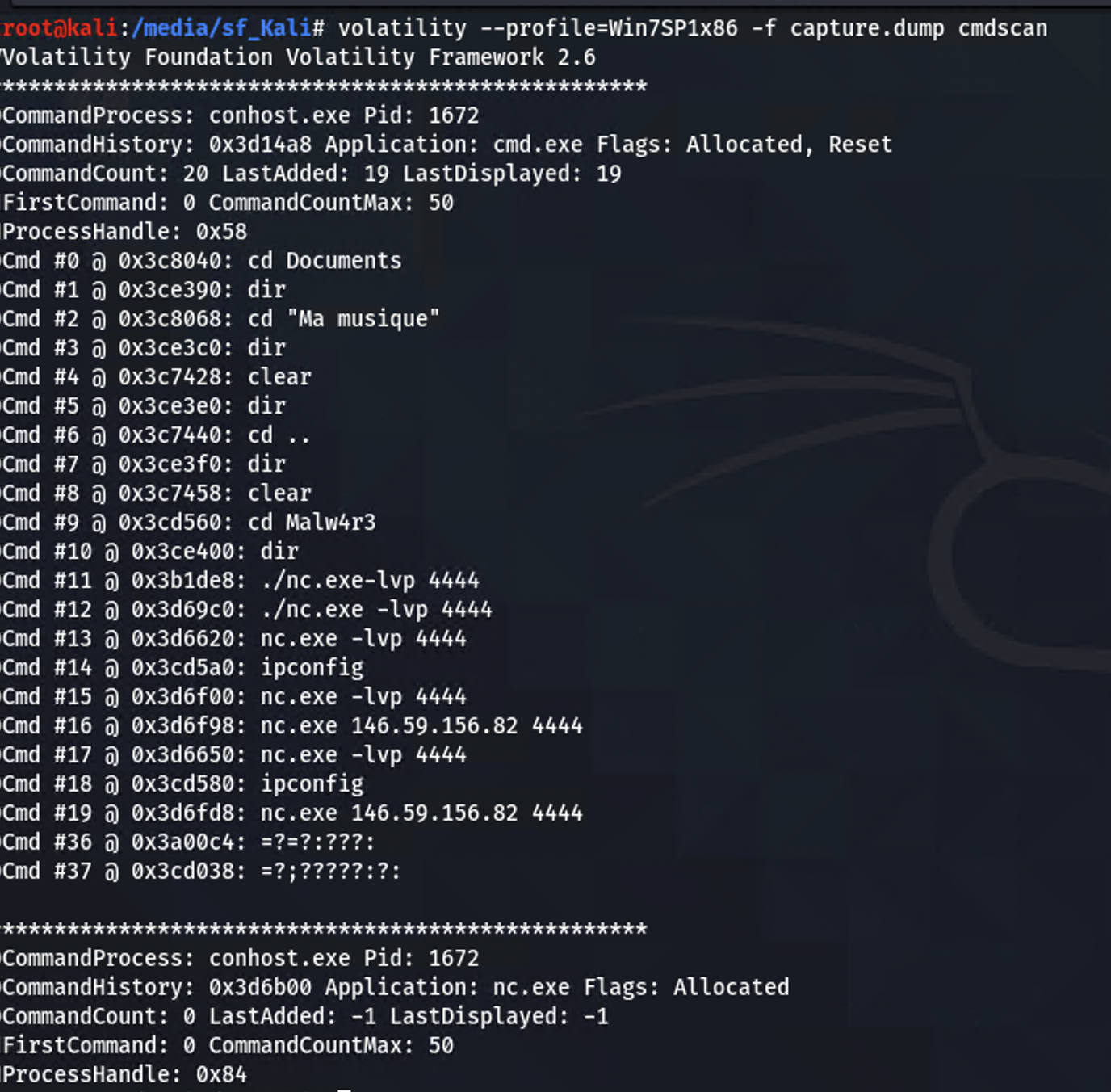
volatility –profile=Win7SP1x86 -f capture.dump cmndscan
Another way, and likely the intended way, to solve this challenge is with the “netscan” module which will check for connections and sockets. After running the command, the ESTABLISHED state shows an existing outbound connection.
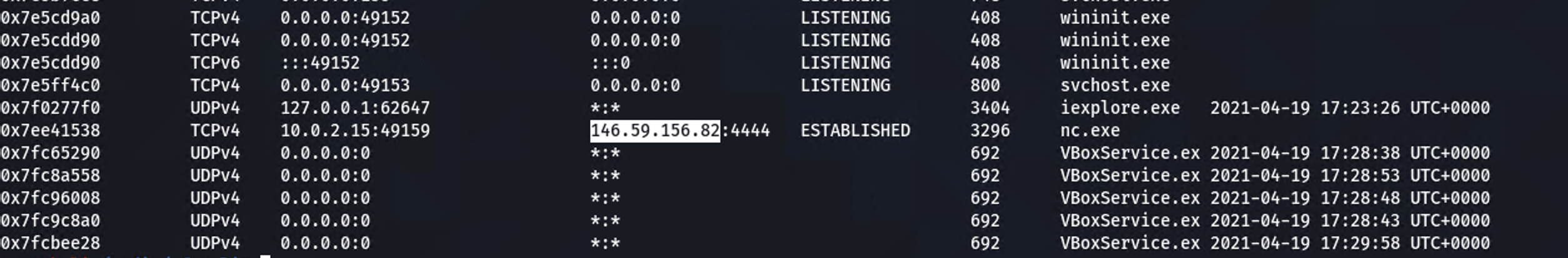
volatility –profile=Win7SP1x86 -f capture.dump netscan
Flag:
Hero{146.59.156.82:4444}
We need you 4/5
This is where the challenge started getting difficult as there were multiple pieces required to solving this challenge.
- Both hacker’s names
- The Name of the Malware
- The version of the malware
The first hacker name is found by extracting the contents of the clipboard from the dump.
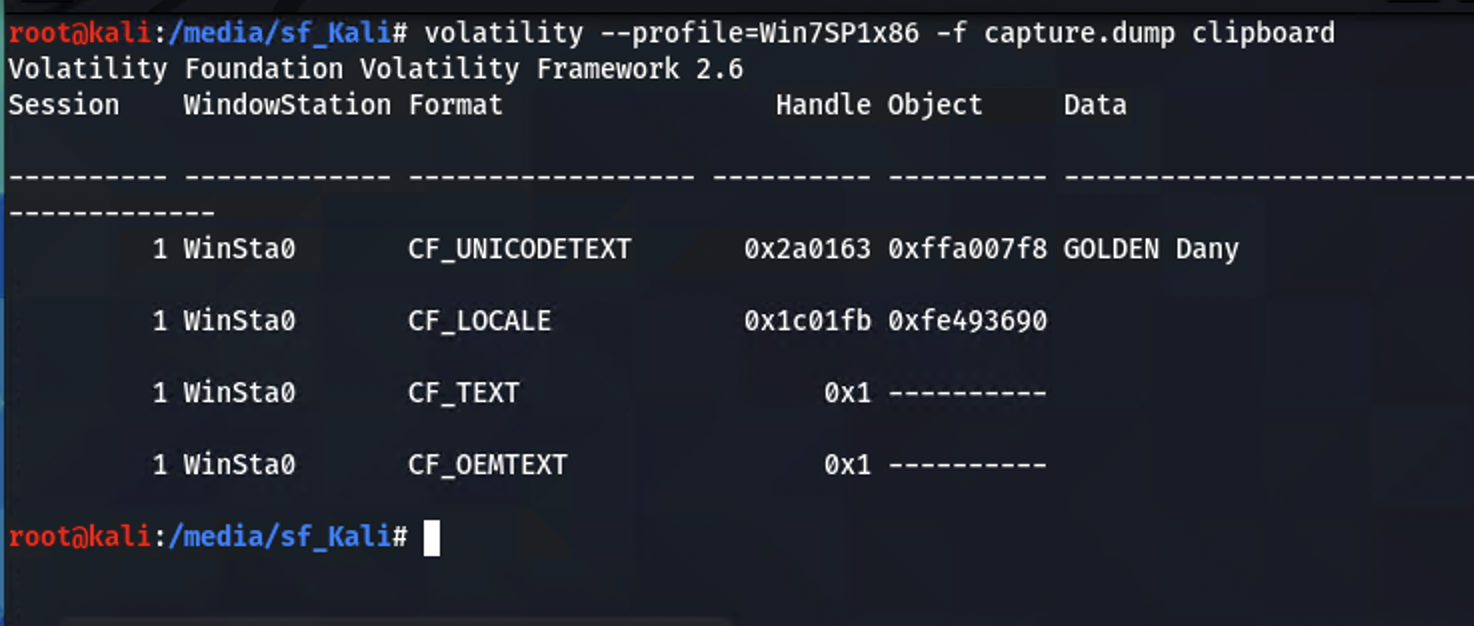
volatility –profile=Win7SP1x86 -f capture.dump clipboard
Finding the name of the malware was tricky. While enumerating the dumpfile, running the consoles module shows the full paths of the working directories the Razex user was operating out of.
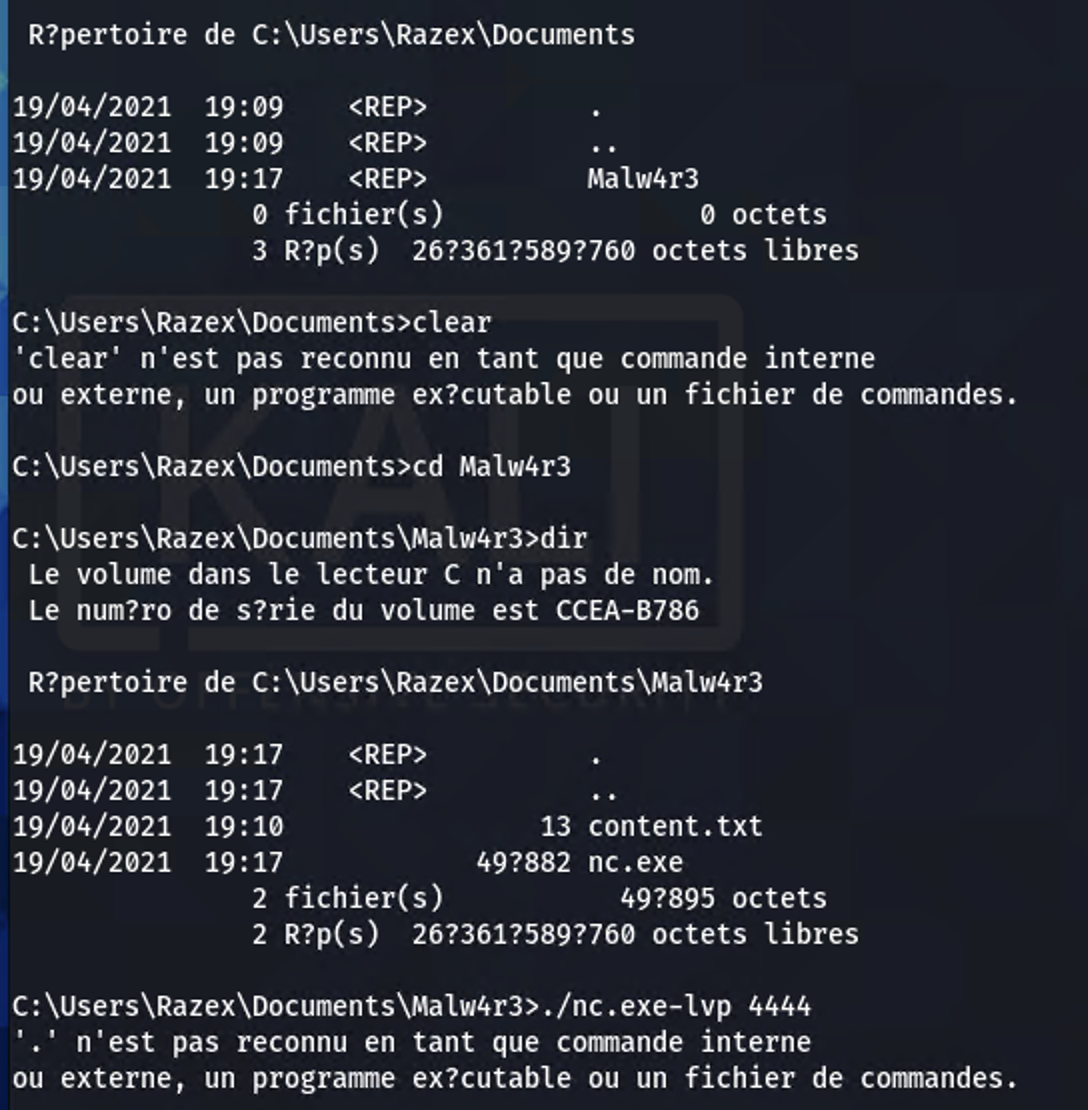
What stands out is the directory “Malw4r3”
Nothing showed up in any of the historical commands modules so I used strings once again to find anything related to that “Malw4r3” string. A suspicious “txt” file shows up in the results
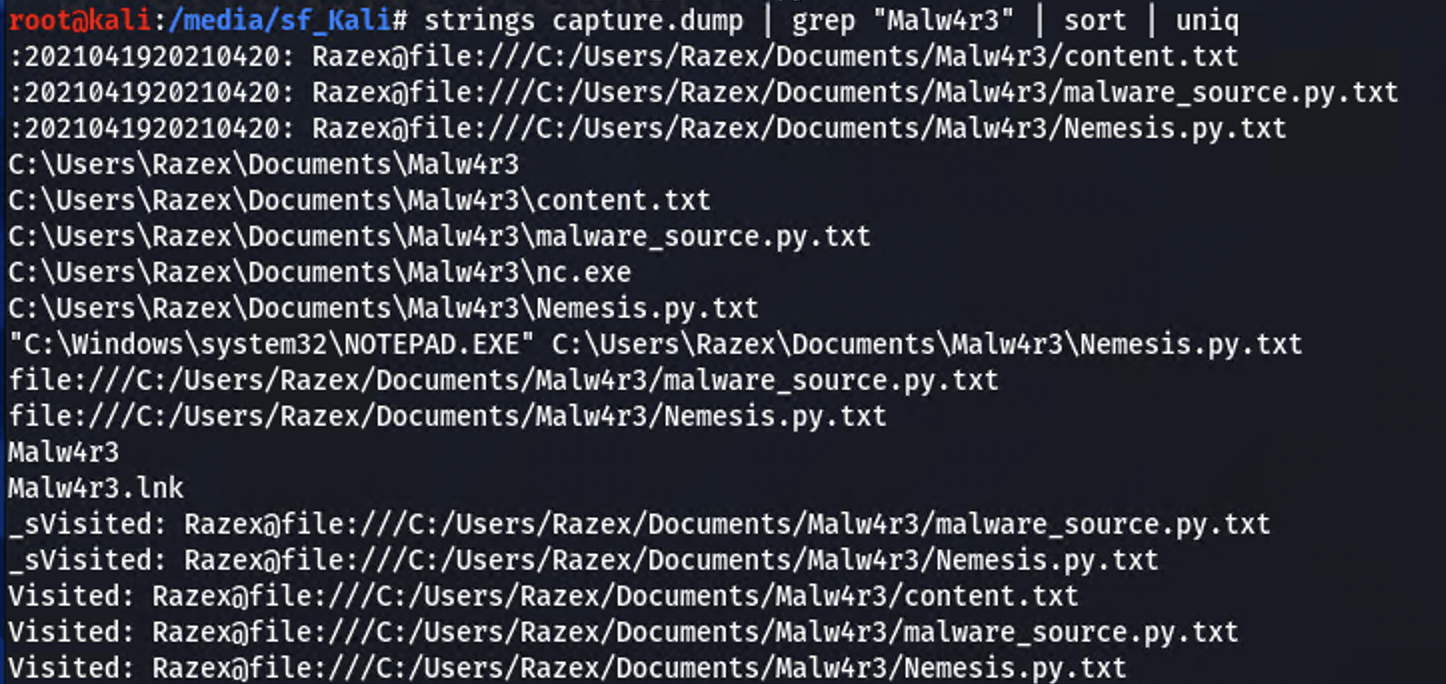
Run the filescan module and grep for the .txt file.
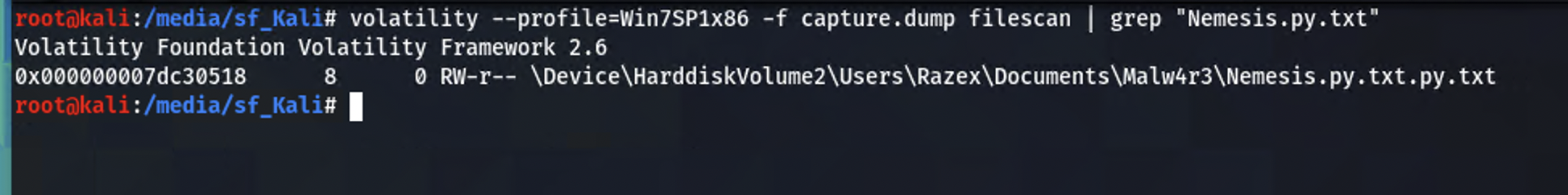
With the physical address of the text file identified, use the dumpfiles module to extract it.
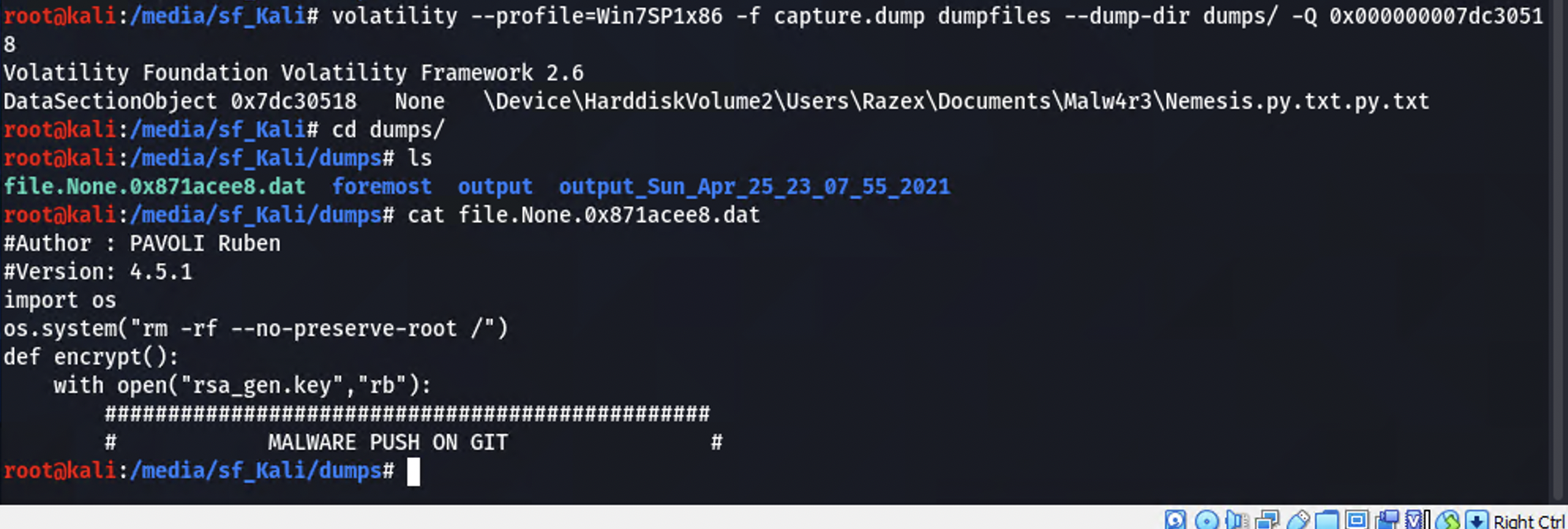
Flag:
Hero{PAVOLI-Ruben:GOLDEN-Dany:Nemesis-4.5.1}
We need you 5/5
The hint from the challenge directs you to check their web browsing history. Using the iehistory module reaveals an onion site.
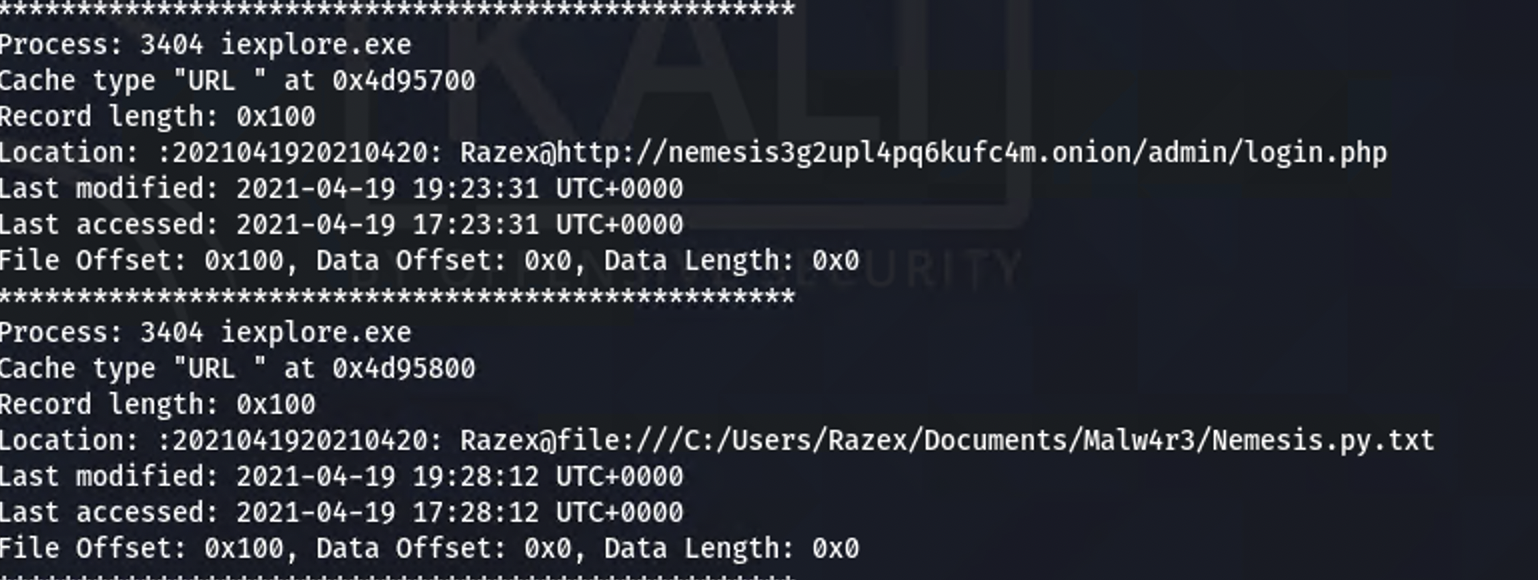
volatility –profile=Win7SP1x86 -f capture.dump iehistory
Building on the iehistory there are two processes of internet explorer identified where interaction with the .onion URL occurred: 3404 and 3504. The dump also supplies the username involved with the activity and can be seen in output.
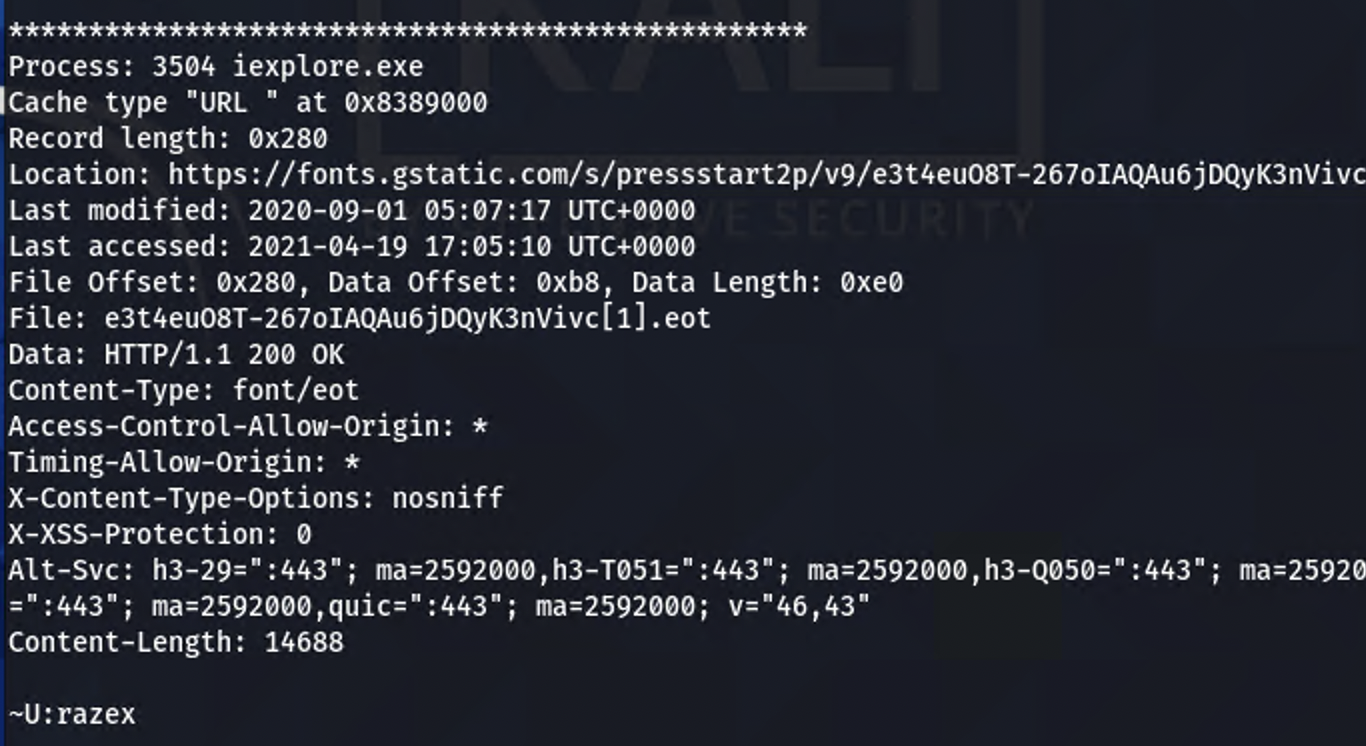
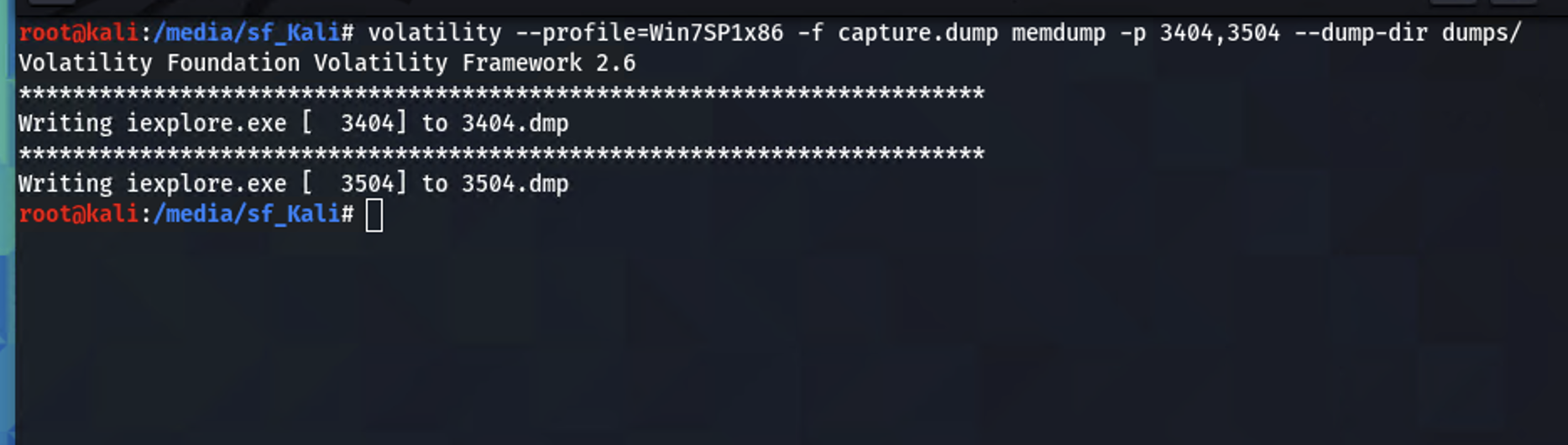
Dump the two IE processes with memdump
The final piece to this puzzle was the password which I just was completely unable to find on my own. I received a hint from another player in Discord to check the encoding options. When setting it to UTF-16 I eventually stumbeled my way to the solution guessing the only thing that slightly resembled a password. The failure on the hacker’s part came from including their username in their password.
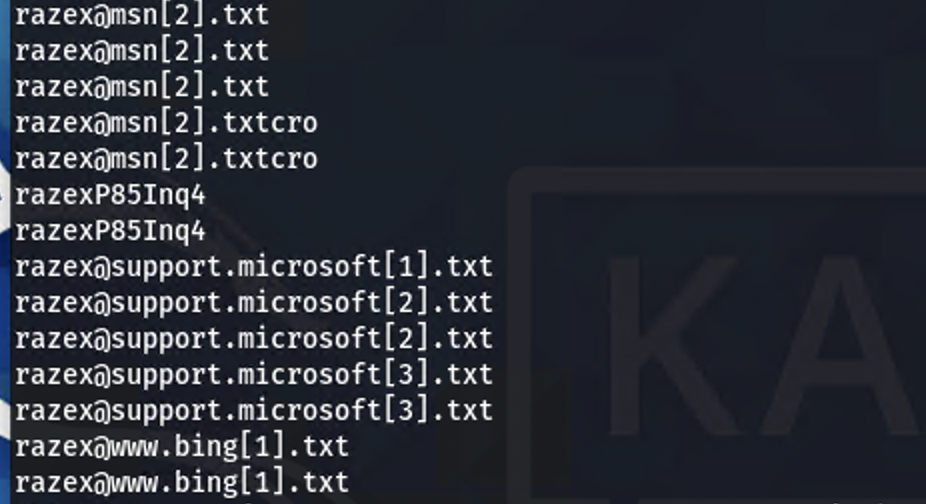
strings –encoding=l 3504.dmp | grep razex | sort
Flag
Hero{nemesis3g2upl4pq6kufc4m.onion-razex:razexP85Inq4}
Thanks Worty for the loss of sleep.